This Linux machine is a bit special compared to other Linux challenges because this is a CentOS operating system.
Add the IP address in /etc/hosts:
...
10.10.10.7 beep.htb
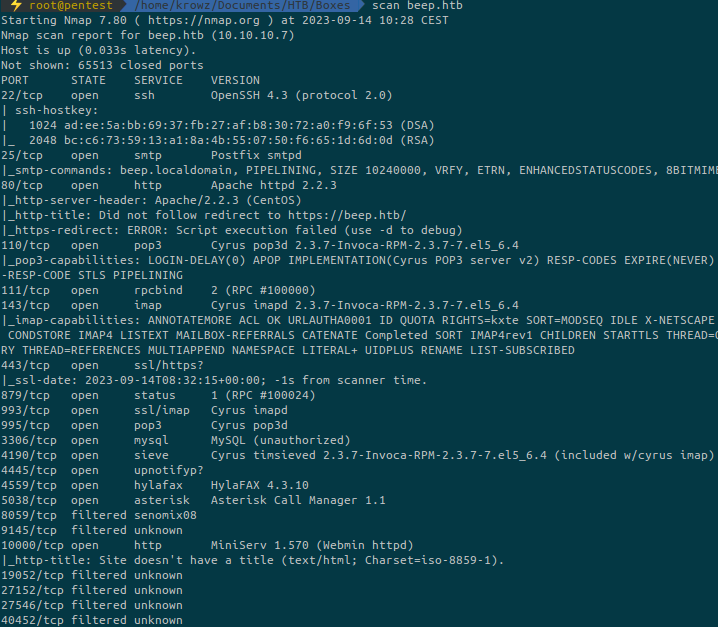
...There is a lot of open ports on this machine. But most of them could be rabbit holes.
If you have absolutely no experience in HTB or CTF in general, the only solution is to check for all version numbers and try exploits.
But here one specific port is very attractive: 10000
It runs Webmin which is very often vulnerable.
If this is not the case, we’ll move on other services and enumerate them.
But let’s start with this one.
Go on Google and search for this webmin version: https://github.com/ruthvikvegunta/CVE-2019-15107
But unfortunately this is not the same version and it is not vulnerable to this.
On the main page of the website port 80 there is a login page:
Fuzzing for the main website:
images [Status: 301, Size: 306, Words: 20, Lines: 10]
index.php [Status: 200, Size: 1785, Words: 103, Lines: 35]
help [Status: 301, Size: 304, Words: 20, Lines: 10]
register.php [Status: 200, Size: 1785, Words: 103, Lines: 35]
themes [Status: 301, Size: 306, Words: 20, Lines: 10]
modules [Status: 301, Size: 307, Words: 20, Lines: 10]
mail [Status: 301, Size: 304, Words: 20, Lines: 10]
admin [Status: 301, Size: 305, Words: 20, Lines: 10]
static [Status: 301, Size: 306, Words: 20, Lines: 10]
lang [Status: 301, Size: 304, Words: 20, Lines: 10]
config.php [Status: 200, Size: 1785, Words: 103, Lines: 35]
robots.txt [Status: 200, Size: 28, Words: 3, Lines: 3]
var [Status: 301, Size: 303, Words: 20, Lines: 10]
panel [Status: 301, Size: 305, Words: 20, Lines: 10]
libs [Status: 301, Size: 304, Words: 20, Lines: 10]
recordings [Status: 301, Size: 310, Words: 20, Lines: 10]
configs [Status: 301, Size: 307, Words: 20, Lines: 10]On Google, if we search for elastix exploit:
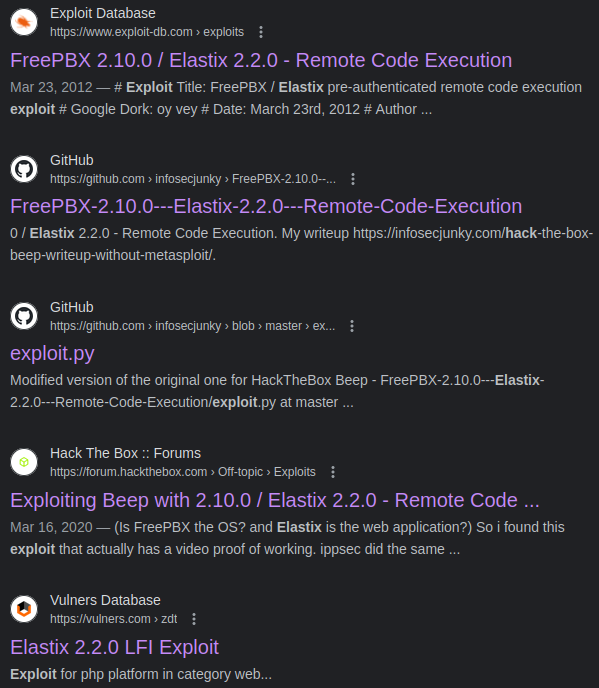
I tried the first three exploits but none of them were working because of SSL errors. Even after disabling SSL in my configuration files and all that stuff.
But the last result on the screenshot is interesting because it tells us there is a LFI vulnerability: https://vulners.com/zdt/1337DAY-ID-19210
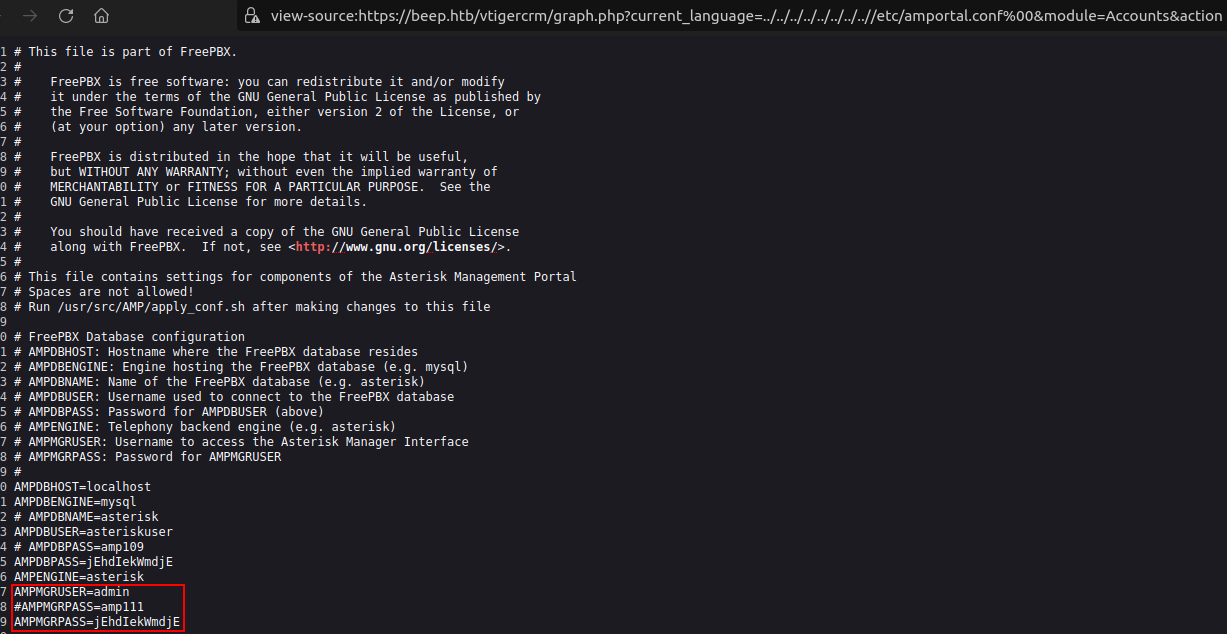
It contains credentials:
admin:jEhdIekWmdjEWe can connect to http://beep.htb/admin with these creds:
But I could get a reverse shell from that. Even with https://github.com/DarkCoderSc/freepbx-shell-admin-module/
So I tried to connect to SSH with the credentials we got earlier and it worked…
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 root@beep.htb -> jEhdIekWmdjESo we’re connected as root and finished the machine!
Then I went to look at writeups to see what I missed.
In fact this HTB machine is like Metasploitable. Multiple paths to get root.
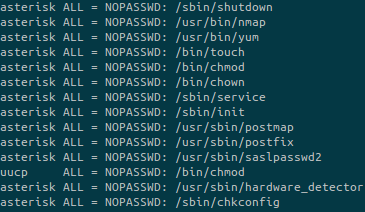
If I had access to the machine as another user, the privesc would have been easy: